HyTrust KeyControl is delivered in multiple formats. Click on the link to refer to the installation instructions that are specific for the media type you are using (Note that AMI and VHD installation instructions appear in the AWS and Azure guides).
The first step is to install an initial KeyControl node. Once a node is installed and set up, most administrative tasks are performed using the webGUI.
The steps needed for setting up HyTrust DataControl are as follows.
| Note: | A 30-day license key is shipped with the product and will be activated when you install and configure the first KeyControl node. This allows you to protect up to 5 virtual machines and use all product features. For further details, see License Management. |
HyTrust recommends that the following system resources be available based on the size of your installation:
|
Resource |
Standard |
Large |
Demo or |
|---|---|---|---|
| CPUs | 2 | 4 | 2 |
| RAM | 8 GB | 16 GB | 1 GB |
| Disk | 20 GB | 60 GB | 20 GB |
The KeyControl appliance detects when there is less than 2 GB of free space, and sends an alert. If you want to increase the size of your drive, use your hypervisor commands to resize the underlying disk.
Next, reboot the KeyControl node. You can do this by using the console.
Upon reboot, review the Audit log messages. The node should report the new size upon success or provide information if the resize failed.
Please note that KeyControl nodes communicate amongst themselves over TCP ports 2525, 2526, and 8443. If you have a firewall between one or more KeyControl nodes in your cluster, you need to make sure that these ports are open.
KeyControl to KeyControl
Policy Agent to KeyControl
HTKC/HTDC communication – Inbound TCP/443 from anywhere there is or will be an HTDC/encrypted client from any HTKC server in the cluster
KeyControl to Infrastructure Services
| Note: | Network ports indicated for SMTP, syslog and NTP are the typical ports for these services, and are configurable. Please consult with the administrators of these services. |
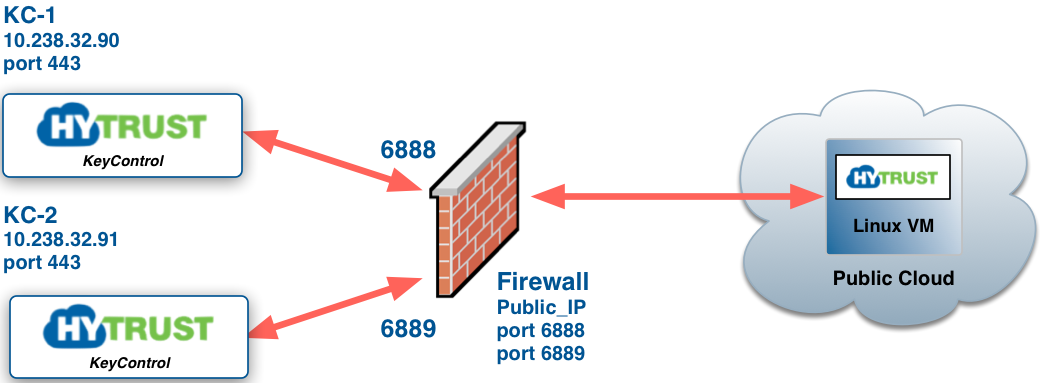
To operate a KeyControl cluster in your data center / private cloud, VMs that operate in the public Cloud using the Policy Agent must be able to communicate with each KeyControl Node. The Agent must also be able to communicate with each KeyControl Node. Consider the following figure:

There are two KeyControl nodes in the cluster with IP address 10.238.32.90 and 10.238.32.91. The VM communicates with them through port 443 (HTTPS). There are multiple ways to achieve this communication, but the simplest way is to map a port in your firewall to each KeyControl node in the cluster and use the firewall IP address / port number when registering the VMs.
You can also consider having a load balancer behind the firewall that exports a single IP address to the firewall (and therefore the VMs) and your KeyControl nodes.
Regardless of the media used for installation, you will need to use the system console menus. These are text-based and involve use of the cursor keys, the <tab> key and the <enter / return> key.
The login on the system console menus is always "root" — you will set the password as you log in for the first time, but the login will not change. Note that this is only for the System Console Menu. The WebGUI requires a separate login.