Managing Clusters
You manage clusters of KeyControl nodes through clicking the Cluster Icon on the home page, which brings up this dialog box:
![]()
Through the settings in this dialog box, you can fine tune your cluster settings in the following ways.
Managing Cluster Settings
On the Cluster tab, you can choose:
- Description: You can describe the cluster, if you wish. This is optional.
- Backup Hosts: Enter the names or IP addresses of host systems that are allowed to NFS mount the backup directory. (0.0.0.0 means any server can have access, as noted earlier.)
- Cluster Operation Timeout: This value is the amount of time that a KeyControl node waits to receive a response from another KeyControl node. If a response is not received by the specified timeout, the KeyControl cluster goes into degraded mode which indicates a network connectivity problem. You should enter a value in the range of 1-30 seconds. By default, the cluster timeout is set to 30 seconds. If a KeyControl cluster frequently switches between degraded state and healthy state, increase the timeout value of cluster operation. Err towards setting the timeout value at a lower number. This ensures that if an operation fails, admins notice it quickly and realize that the cluster is in degraded state.
- Allow Reconnect: the default is Yes, to allow reconnect.
- Require Authentication Passphrase: The default is Yes, to require an authentication passphrase.
- Hide Authentication Passphrase Entry: the default is No, so that the user can see what is being typed.
- Check Hardware ID: the default is Yes, to validate the hardware ID.
On reconnect (if reconnect is allowed, see above) we check a collection of hardware signatures to validate that a node is indeed the same as we expect. If this tunable is checked, then this ID is checked each time a reconnect happens. If it is not checked, this ID is not checked. If reconnect is rejected, authentication has to be redone for the node.
NOTE: This should only be disabled in very, very secure environments. Even in these environments it should be left checked unless it is known that machines will be moved around frequently.
Make sure your settings are accurate, and then click Save after each one.
Nodes that have been authenticated successfully will, when restarted, attempt to automatically reconnect to the KeyControl cluster. If this choice is set to Yes, then such attempts are allowed (subject to hardware ID check, see below). If it is set to No, then no reconnect is allowed and an admin has to redo authentication any time a node restarts. Note that you change status by checking and clearing a checkbox.
NOTE: This is a security feature and the default is most permissive. To strengthen security, clear the checkbox to NOT allow reconnection. This will be probably considered too painful by any but the most paranoid.
NOTE2: The exception to reconnect is when you have a single node KeyControl "cluster", and thus there is no one to reconnect to. A restart of such a KeyControl node has no one to validate against and thus works regardless the choice you make here.
Initial authentication performs a handshake between a new node and an existing KeyControl cluster. If this option is set to Yes, a one-time passphrase will be required on both ends to give an out-of-band assurance that the node is valid and should be allowed to join. If it is not checked, then no passphrase is required and joining the node is assumed valid. Note that you change status by checking and clearing the checkbox.
NOTE: This is a security feature and the default is the strongest choice. It should only be set to No in a very secure environment.
If a passphrase is required, it is entered both on the console and in the GUI. The passphrase is for one-time use in a very short window and is therefore not something that generally needs the heaviest security. If this option is set to Yes, passphrase entry on the console is not echoed and requires a second entry for verification. If it is set to No, passphrase entry on the console is echoed back to the user and only a single entry is needed. Note that you change status by checking and clearing a checkbox.
NOTE: The webGUI entry is never echoed. The passphrase is checked immediately and if it is not correct, re-entry is required.
Managing KeyControl Servers
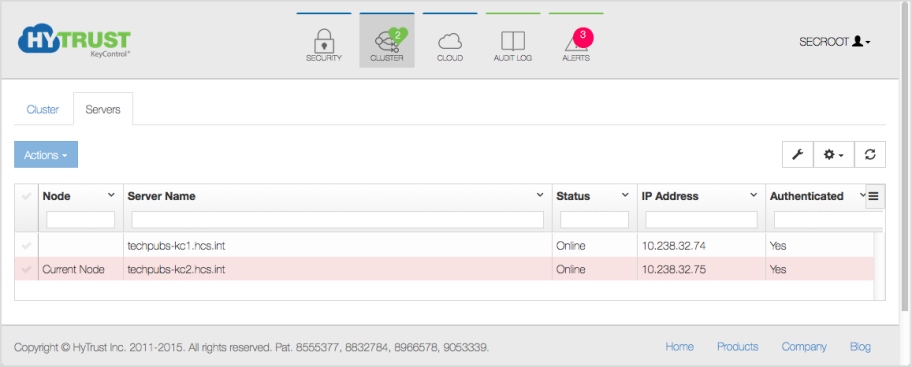 On the Servers tab, you can check the online and authentication status of individual servers, sort them by a variety of fields, and search for servers using the grid.
On the Servers tab, you can check the online and authentication status of individual servers, sort them by a variety of fields, and search for servers using the grid.
See also: Using the Grid to Find and Edit Material
See also: KeyControl Clustering and Upgrade