Encrypting Linux Root and Swap Drives
Introduction
In addition to encrypting regular data partitions, you can also encrypt your root and swap partitions. In addition to encrypting data partitions, encrypting root and swap partitions ensures that clear-text data never leaves the VM on its way to storage. This prevents virtualization and storage admins from being able to view the data.
Requirements
A separate boot disk is required on which the HyTrust Bootloader software will be installed. This allows the system to boot and communicate with HyTrust KeyControl and get the necessary encryption keys. The encryption keys are used to boot and decrypt (on the fly) the Linux root disk / filesystem and encrypt/decrypt swap device.
Make sure your version of Linux has a separate boot partition. If it does not you will need to create a separate boot disk. For information on Ubuntu, CentOS 6, and CentOS 7, see Preparing a Linux VM for Root and Swap Drive Encryption
If the Linux installation does not have separate boot partition, you will need to add a new disk device or create a free partition on the existing device, as described in the sections linked to above.
Getting Ready to Encrypt
First of all, let's see what disks we currently have:
# hcl status Summary --------------------------------------------------- KeyControl: 10.238.32.74:443 KeyControl list: 10.238.32.74:443 Status: Connected Registered Devices --------------------------------------------------- Disk Name Clear Cipher Status --------------------------------------------------- Available Devices --------------------------------------------------- Disk Name Device Node Size (in MB) --------------------------------------------------- Other Devices --------------------------------------------------- Disk Name Device Node Status --------------------------------------------------- sda3 /dev/sda3 Mounted (swap) sda2 /dev/sda2 Mounted (/boot) sda1 /dev/sda1 Mounted (/)
You can see that the VM is registered with the KeyControl server (Status shows Connected), there are the root (/) and swap devices that we want to encrypt and you can see that there is a separate boot disk. The root and swap disks are listed under Other Devices since they are in use. Usually, the hcl command is used to add/encrypt disks but root and swap are special cases and require use of the htroot command.
NOTE: In the process of root encryption, we will prepare the system for encryption and then prompt you for a reboot. It is imperative that either the IP address of the VM is static, or if you have dynamic IP addresses and you turn off Reauthenticate on IP Change. For example, in the following figure:
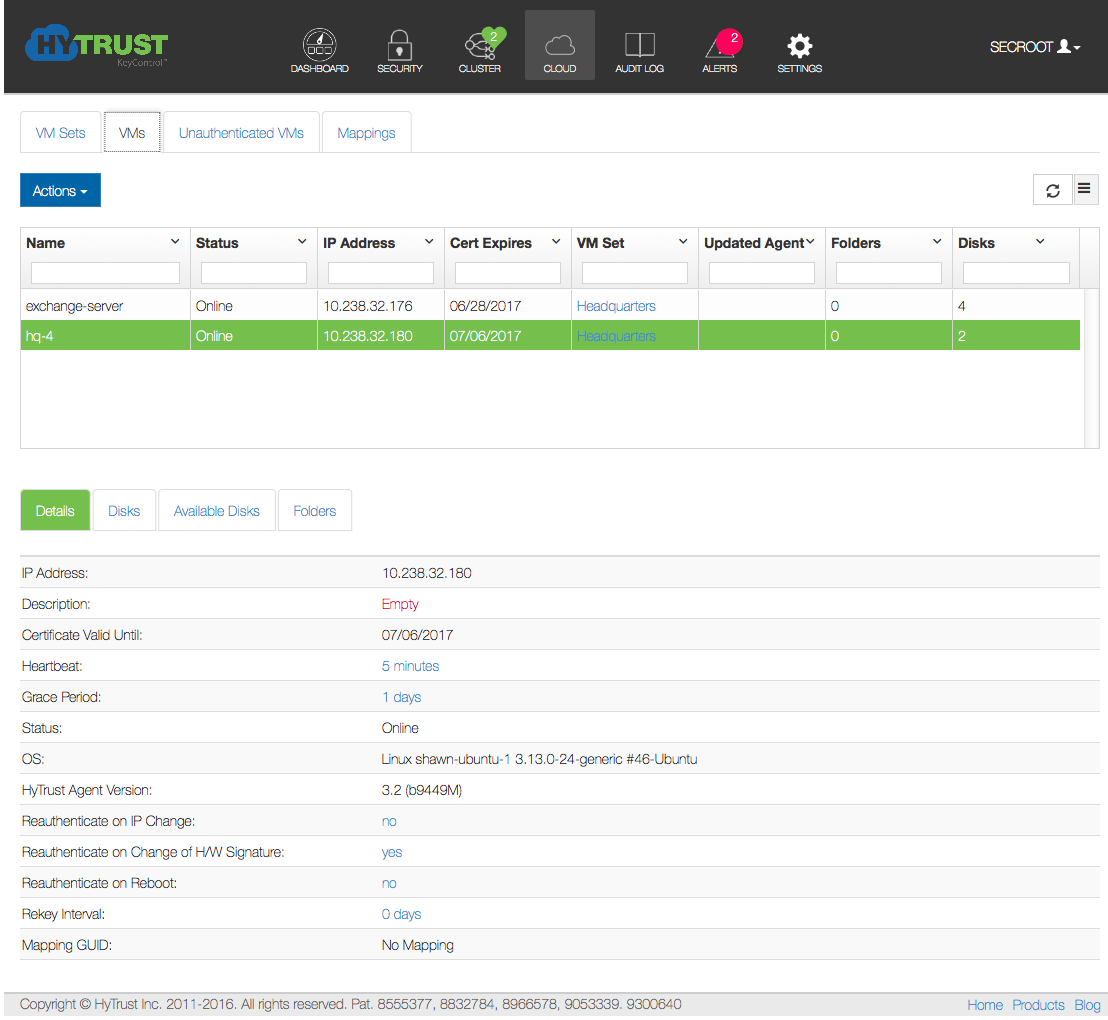
We have a Linux VM called "hq-4."
If you do not have a static IP address, check the VM with "hq-4", and in the Details area, make sure to uncheck the Reauthenticate on IP change line. This change takes effect immediately.
Thus, when the VM reboots it will still be able to authenticate. This is very important to understand.
If you do not have a static IP address and the VM reboots during the root encrypt cycle, you could end up with a hung system.
If you fall victim to this problem (you have a dynamic address and you forgot to uncheck the box) you can still do so after the VM reboots.
We strongly recommend that you use static IP addresses (or DHCP with static) when using Linux root encryption.
Selecting the Root and Swap Disks for Encryption
Once you are certain that you have network IP address and authentication steps correct, it is time to select the disks for encryption. For this, you use the htroot command. For example, the following set of steps selects both root and swap devices for encryption. Note that it may take a little while to download and install any necessary packages that are needed.
# htroot encrypt Debug console can be used to monitor the progress of root device encryption The following packages are required for debug console: dropbear Do you want to enable debug console? (y/N) y The following packages are required for root encryption: busybox dropbear Attempt to install required packages? (y/N) y Updating aptitude repository Checking necessary packages Installation successful Current Root device/ Boot device setup -------------------------------------------------------------------------------- Root device sub1504--vg-root Root device path /dev/mapper/sub1504--vg-root Boot partition device path /dev/sda1 Boot partition device uuid afb1fa83-9902-4e15-8dd3-5a497a3584f8 swap device sub1504--vg-swap_1 swap device path /dev/mapper/sub1504--vg-swap_1 -------------------------------------------------------------------------------- Is this information correct? (y/N) y Do you want to encrypt swap? (y/N) y Following network interfaces are available -------------------------------------------------------------------------------- eth0 00:0c:29:e4:a5:e9 192.168.13.200 -------------------------------------------------------------------------------- Preferred Network Interface is (eth0), which is used while authenticating with KeyControl Select the primary interface (eth0): This machine seems to be using DHCP to setup the primary network With encrypted root device, KeyControl needs to be contacted during boot to get the encryption keys. IP address can be obtained using DHCP or can be statically configured now Use DHCP during boot? (y/N) y Setting up system for root device encryption. This operation may take a long time Do you want to proceed? (y/N) y Re-structuring HyTrust specific directories Please copy the keyfile /etc/initramfs-tools/root/.ssh/id_rsa to another machine This file will be used to access debug console using ssh example: # ssh -i id_rsa root@server.ip.addr Have you copied the key file? (y/N) y Updating initramfs Changing /etc/fstab to mount file system / from /dev/mapper/clear_htroot Changing /etc/fstab to mount the swap from /dev/mapper/clear_htswap The system has been updated to encrypt the root device during nextboot; please reboot the system now Do you want to reboot the system now? (y/N) y Broadcast message from root@13 (/dev/pts/0) at 17:20 ... The system is going down for reboot NOW! Connection to be closed by remote host.
Mostly, you will be confirming steps taken during the process. Once completed, you will be asked to confirm rebooting the system. Once rebooted, HyTrust DataControl will authenticate against the KeyControl server to get the required keys and then start the root encryption process. The length of time taken will depend on the size of the root disk and the type of storage you have. We recommend that you run on a system with AES-NI support which will decrease the amount of time to encrypt significantly.
Please take note of the question asked:
Do you want to enable debug console? (y/n)
We recommend you enter y, in which case we will set up SSH access to the running system while encryption is taking place.Since encryption can take a fair amount of time, it is useful to have the ability to SSH to the server and view progress. We shall talk about debug access in the next section.
Once encryption of root has completed, you will be able to log in as you normally do. Subsequent boots take the normal amount of boot/reboot time.
Running hcl status will show that the root and swap disks are now under HyTrust control:
Registered Devices --------------------------------------------------- Disk Name Clear Cipher Status --------------------------------------------------- sda5 /dev/mapper/clear_sda5 AES-256 Attached '--> auto_attach=ENABLED, attach_handler=DEFAULT, detach_handler=DEFAULT sda1 /dev/mapper/clear_sda1 AES-256 Attached '--> auto_attach=ENABLED, attach_handler=DEFAULT, detach_handler=DEFAULT
Recall that /dev/sda1 is the root device and /dev/sda5 is the swap device.
Here we show the clear path access to each of these devices through the /dev/mapper/clear_<device>.
You should not under any circumstance use the direct /dev/sdb interfaces, as you will be accessing the encrypted devices directly and could cause corruption.
You can also view the encrypted root device through the GUI as with other disks:
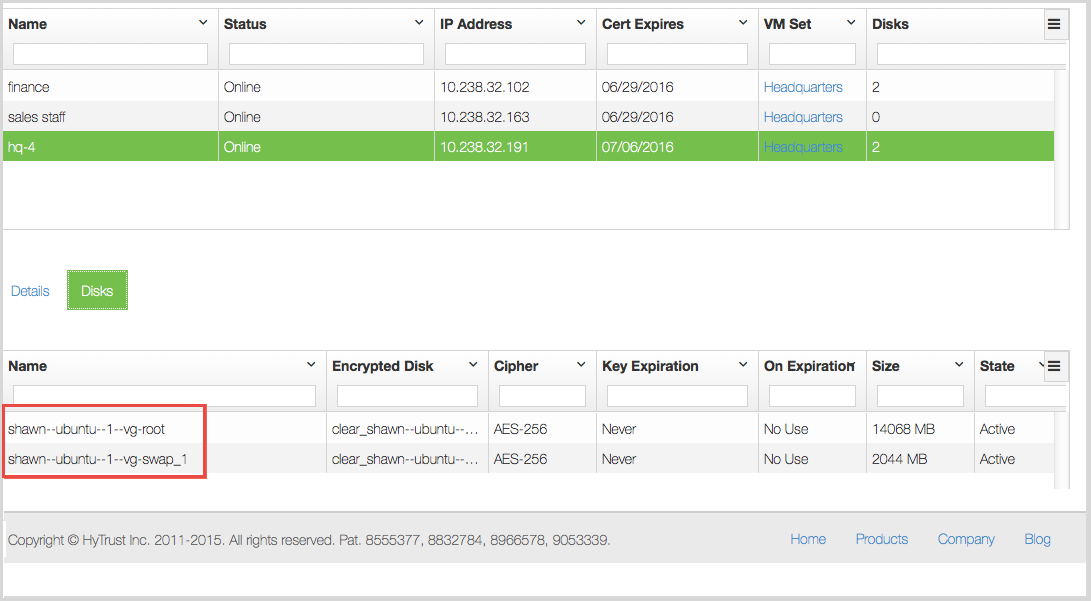
Using the Linux Root Encryption Debugger
When the system reboots and starts encryption, you may want to enter the debug session to determine where the system is within the encryption process. You can SSH to the server using the key obtained earlier. For example, here we run SSH and show the menu that is displayed:
# ssh -i id_rsa root@192.168.140.133 Warning: Permanently added '192.168.140.133' (RSA) to the list of known hosts. BusyBox v1.20.2 (Ubuntu 1:1.20.0-8.1ubuntu1) built-in shell (ash) Enter 'help' for a list of built-in commands. HyTrust Debug Console 1. Show HT encryption log file 2. Authenticate 3. Show Network info 4. Restart Network 5. Advanced access 6. logout Action:
The first option is the most important. It will display the encryption status. For example, here are a few of the lines towards the end of the output:
------------ KeyControl and status ----------------- 192.168.140.151:443 Connected --------------------------------------------------- ------------ Encryption / Decryption status -------- Root device encryption Processing: 21% Time left: 00:13:53 ---------------------------------------------------
We can see that we are connected to the KeyControl server and that encryption is in progress. At this point, the operation is 21% complete and there are just under 14 minutes left.
You should not need to invoke any of the other operations unless required by HyTrust support.
Once encryption has completed, you will get the login prompt as you normally do.
Rescue Authentication
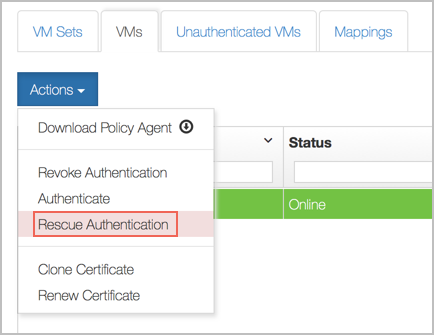
If a root-drive-encrypted VM goes in to the unauthenticated state, it can still be authenticated by taking these steps:
- Click the Cloud Icon.
- Select the VM you want to authenticate.
- Click Actions, and then click Rescue Authentication.
This simplifies the authentication process for virtual machines in the public cloud, such as AWS, Azure, where the admin can see the boot log, but cannot access the console.
The root-drive-encrypted VM periodically tries to heartbeat with the KeyControl. After the Rescue Authentication button is pressed, the next heartbeat brings the VM to an authenticated state.
Note that Rescue Authentication is different from the regular Authentication button. It only works during the VM boot process. If the root drive is not encrypted, then the Virtual Machine stops the heartbeat after a couple of tries. After this, the admin can authenticate the VM only with the regular Authenticate process, as described in "Revoking VM Permissions", in the section "Encryption Within Virtual Machines, Using the DataControl Policy Agent"