Logging and Auditing
Contents
Introduction
There are three top-level categories of audit records:
- Security Administration audit records
- Domain Administration audit records
- Cloud Administration audit records
Security Administrators are able to view all audit records. Other administrators are only be able to access audit records for the administrative groups for which they are members. For example, assume that there are two Cloud VM Set groups "HR" and "Legal" and that:
- Joe is a Cloud VM Set Admin in the "HR" group.
- Bill is a Cloud VM Set Admin in the "Legal" group.
Any activity with in "HR" group that generates audit records will be visible by Joe but not by Bill. Likewise, any activity within the "Legal" group that generates audit records will be visible by Bill but not by Joe. Both Joe and Bill will not see audit records generated as a result of activity in any VM group for which they are not members as with any non-VM group and any Security Administrator actions.
Viewing Audit Records
The audit records that are visible to a specific administrator can be viewed by clicking the Audit Log icon at the top of each screen as follows:
To see the details of a particular record click in the left column. A green check-mark appears, and the audit record shows beneath, as follows:
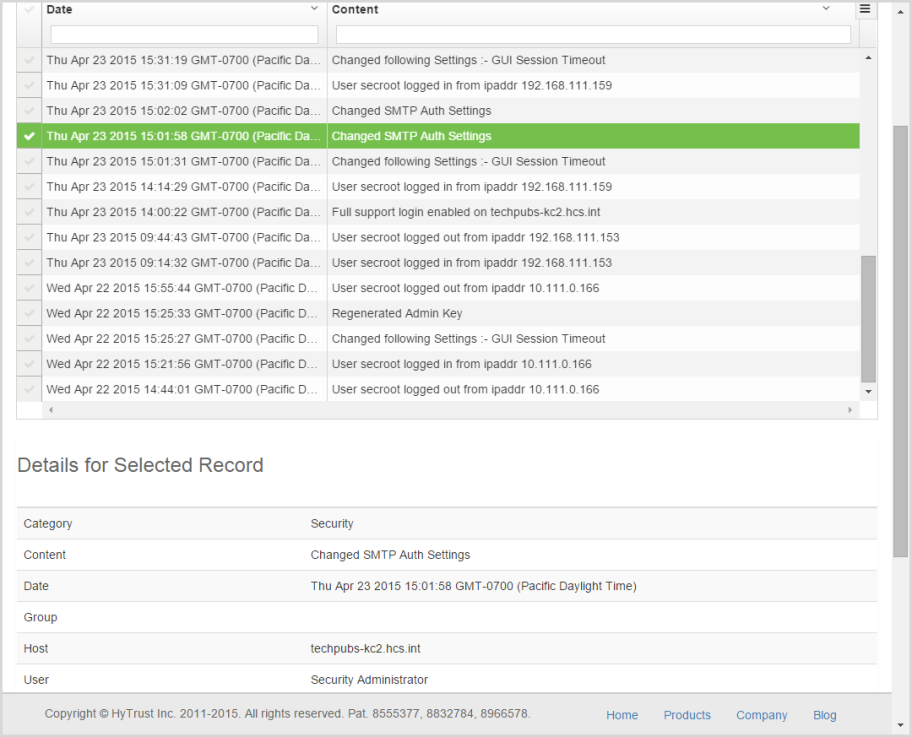
To search for a particular audit record, use the search tools built into the grid, as described in Using the Grid to Find and Edit Material.
To export the audit log to a file, click the Actions Button, and then click Export. You receive the following screen to fill out. When ready, click Generate. Note that you can specify Format type, rows, and columns to export.

To upload the audit log, click the Settings Icon, and then click Send Logs.
The downloaded audit file is XML-formatted. Each audit record is referenced by the tag <AuditRecord>. An example of the audit record displayed above is shown below:
<AuditRecord><timestamp>1429826518</timestamp><category>Security</category>\
<host>techpubs-kc2.hcs.int</host><username>Security Administrator</user_name><message>\
Changed SMTP Auth Settings</message></AuditRecord>
Exporting audit records to an external syslog server
Audit records can also be posted to an external log server through the standard syslog protocol. To configure this support, from the Settings Icon tab, select Audit Log and then fill in the appropriate information in the form below.

The syslog server should be configured to allow messages to be received from each of the KeyControl nodes in the cluster. The syslogd flags that specify the KeyControl nodes should specify names that are resolvable. Either make sure that your /etc/hosts file is set up correctly, that you enter IP addresses for your KeyControl nodes or if you use hostnames, ensure that reverse lookups work on the syslog server.
Audit messages will be tagged with hcs_audit and should be added to your syslog.conf file. The FreeBSD example below directs all hcs_audit messages to go to the log file /var/log/hcs_audit.log:
!hcs_audit
*.* /var/log/hcs_audit.log
!-hcs_audit
You should create the file and make it writeable by root only. For example:
# touch /var/log/hcs_audit.log
# chmod 0600 /var/log/hcs_audit.log
You will need to configure your rc.conf file. For example, the following should be set prior to changing to syslog.conf:
syslogd_enable="YES"
syslogd_flags="-a kps1.domain -a kps2.domain -v"
You should restart the syslog daemon and audit records generated by any KeyControl node should get written to the hcs_audit.log file. For example, you can test easily by simply logging out and back in again. This will generate two audit records. Displaying the last part of the hcs_audit.log file will display entries similar to:
<AuditRecord><timestamp>1429737024</timestamp><category>Security</category> \ <host>techpubs-kc2.hcs.int</host><user_name>Security Administrator\ </user_name><message>Created group KeyControl Admin Group</message></AuditRecord>
<AuditRecord><timestamp>1429737024</timestamp><category>Security</category> \ <host>techpubs-kc2.hcs.int</host><user_name>System</user_name> \ <message>Begin System Initialization</message></AuditRecord>
We recommend that you consult the syslog server settings on your server to ensure that things are set up correctly. If you have set syslog up and still fail to see messages arriving in the hcs_audit.log file, try using tcpdump to make sure that packets are in fact arriving at the server.
See also: Sending Logs to Support.