This chapter describes support for encryption within individual Virtual Machines (VMs) or physical servers wherever they reside (data center, private, public or hybrid clouds). For virtual machines, the HyTrust DataControl Policy Agent has been validated on Windows and Linux VMs on VMware vSphere, Amazon Web Services (AWS), Microsoft Azure and IBM SoftLayer.
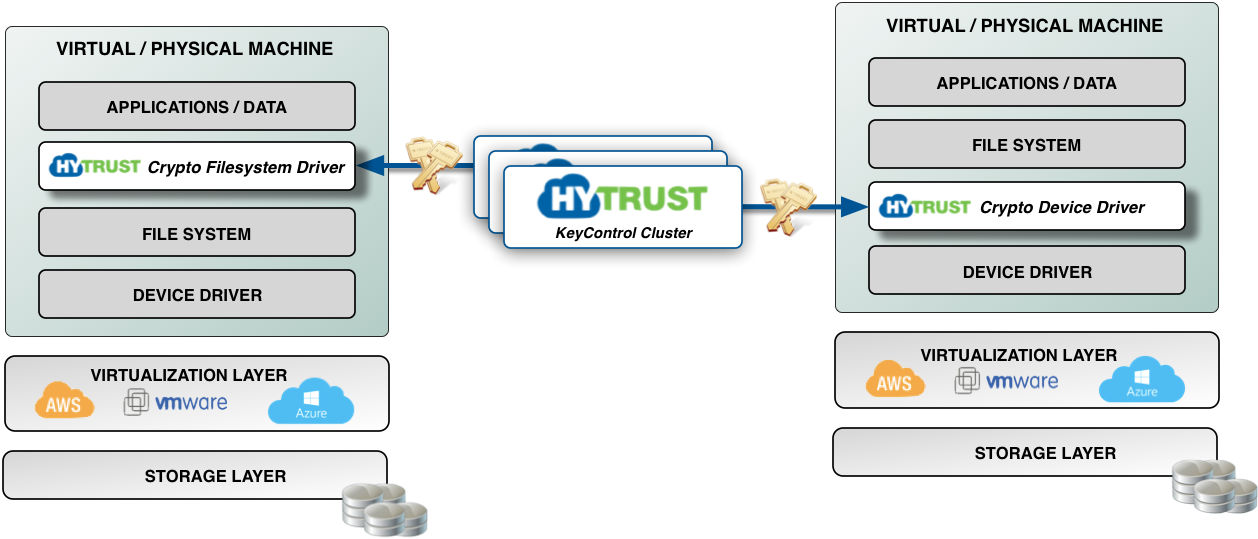
The following figure provides a high-level view of the main architectural components of HyTrust DataControl:

HyTrust provides encryption and key management for virtual and physical machines. The major components are:
KeyControl nodes contain FreeBSD as the core operating system, described in more detail below.
The base of every KeyControl node is the HyTrust-hardened version of FreeBSD, a light-weight, locked-down operating system that has no run-time login/SSH access to the system, to prevent tampering or attempts to access clear-text data and/or encryption keys. Each KeyControl node can be installed as a virtual machine or can be installed on physical (x86-based) hardware.
The main features:
At the heart of every DataControl deployment is an active-active cluster of KeyControl nodes that manage encryption keys for virtual/physical machines. All administration takes place from a standard web browser to any node in the KeyControl cluster or from a set of REST-based APIs.
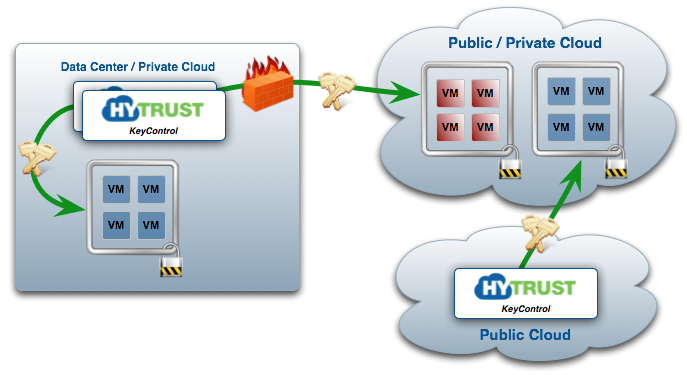
KeyControl features include:
Administration of the system takes place through the KeyControl webGUI, an administration console accessible through a standard web browser.
Access to the webGUI is over HTTPS and works with the latest version of standard browsers (tested with Safari 9 and above, Internet Explorer 10 and above, Chrome 47 and above, and Firefox 42 and above). The full online help includes all guides, and is accessible by clicking Help, found in a drop-down menu under the user’s login name at the top right of the screen.
HyTrust provides a remote CLI (hicli), REST API, and Python API. This enables you to programmatically manage users and groups within the KeyControl cluster and also to manage encryption within virtual machines.
HyTrust KeyControl provides a rich administrative framework that can be leveraged by multiple organizations of different sizes. This approach is useful for organizations ranging from the single-administrator IT shop to a large, multi-tenant cloud service provider who needs to support secure customer environments.
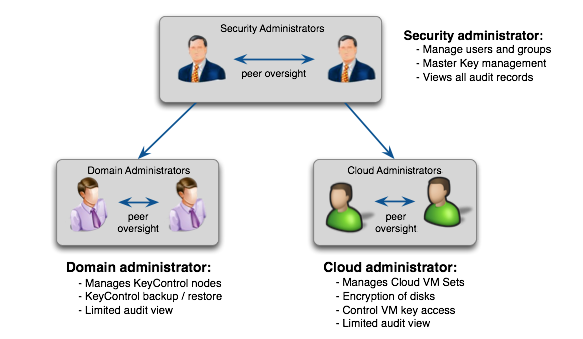
The administration model provides for:
There are three major roles that can be assigned to a user. One user can have one, two, or all of these roles.
Security Admin
Domain Admin
Cloud Admin
Managing encryption keys can be painful and makes encryption difficult to deploy and manage for many organizations. HyTrust KeyControl provides strong encryption technology without the need for users to be experts on key management. Wherever possible, the internals of key management are taken care of in the background.
Ciphers must be specified when disks are encrypted, or keyIDs and FSIDs are created. Otherwise, AES-XTS-512 is the default cipher that is used by the Policy Agent.
For Policy Management encryption keys:
AES 128/256/512-bit encryption support (CBC and XTS cipher modes). Specifically:
| Algorithm | Mode | Key size | Notes |
|---|---|---|---|
| AES-128 | CBC | 128-bit | Not available on Windows boot drives |
| AES-256 | CBC | 256-bit | |
| AES-XTS-256 | XTS | 128-bit | Not available on Windows boot drives |
| AES-XTS-512 | XTS | 256-bit | Not available on Windows boot drives |
For details on the processors that support AES-NI, please view this Wikipedia summary. For details on AES-NI, see this Intel site.
To determine whether your particular computer supports AES-NI, open a command-line window and issue the following command on Windows:
Note: in the command-line interface, your input appears in bold monospaced type.
# hccmd aesni-check
Your system responds with an explicit statement:
AES-NI detected. or AES-NI not detected.
On Linux, issue the command:
# grep aes /proc/cpuinfo
If AES-NI is not available, nothing is returned. If it is available, an "aes" flag displays:
# grep aes /proc/cpuinfoflags : ... ssse3 cx16 sse4_1 sse4_2 popcnt aes ... dts
Any new nodes (KeyControl node or VMs using DataControl) must be authenticated. As part of install, a passphrase is required on the new node, which must also be provided to a KeyControl node within the cluster. This one-time passphrase allows the nodes to establish a secure channel over which certificates are exchanged allowing for secure subsequent communications.
The HyTrust KeyControl Cluster provides secure communications among all nodes:
The HyTrust DataControl Policy Agent provides for encryption of disks, filesystems and files within a virtual machine.
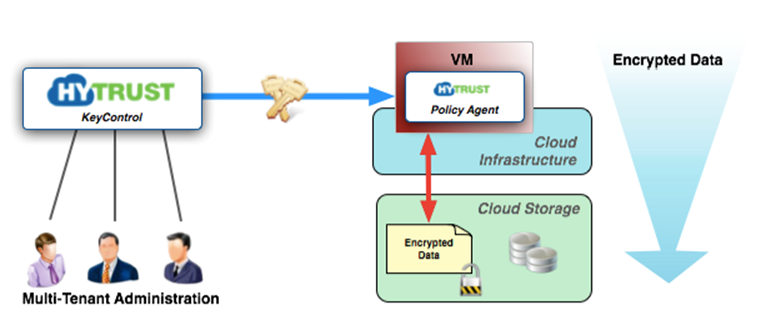
There are a number of features provided in the Policy Agent including:
HyTrust has currently tested on the following Linux and Windows platforms for encryption of devices. We do not support 32-bit versions. Note that all Windows operating systems listed below are supported on AWS and Azure.
| Platform | Data Encryption | Root/System Drive Encryption |
|---|---|---|
|
CentOS 5.10-5.11 |
Yes |
No |
|
CentOS 6.2-6.8 |
Yes |
Yes |
|
CentOS 7.0-1406, 7-1503, 7-1511 |
Yes |
Yes |
|
RHEL 5.10-5.11 |
Yes |
No |
|
RHEL 6.2-6.8 |
Yes |
Yes |
|
RHEL 7.0-7.2 |
Yes |
Yes |
|
Ubuntu 12.04.05 |
Yes |
Yes |
|
Ubuntu 14.04 |
Yes |
Yes |
|
Ubuntu 15.04 |
Yes |
Yes |
|
Ubuntu 16.04 |
Yes |
Yes |
|
AWS Amazon Linux 2015 (PV and HVM) |
Yes |
Yes |
|
Microsoft Windows 7 |
Yes |
Yes (boot drive encryption) |
|
Microsoft Windows 8, 8.1 |
Yes |
Yes (boot drive encryption) |
|
Microsoft Windows 10 |
Yes |
Yes (boot drive encryption) |
|
Microsoft Windows Server 2008 R2 |
Yes |
Yes (boot drive encryption) |
|
Microsoft Windows Server 2012 |
Yes |
Yes (boot drive encryption) |
|
Microsoft Windows Server 2012 R2 |
Yes |
Yes (boot drive encryption) |
If the version of Linux you are running is not listed above, please contact us at info@hytrust.com and provide us with information about the version of Linux and the problems seen.
In VMs with the Policy Agent installed, we support the ability to share KeyIDs (encryption keys referenced by a symbolic name) between VMs within the same Cloud VM Set. This allows you to encrypt data and move it securely between these VMs. Only the VMs within the same Cloud VM Set as the KeyIDs are able to decrypt the data. Encryption is on a file-by-file basis, so movement of larger amounts of data can be achieved by zipping/tarring groups of files and then encrypting them.
These mechanisms can also be used to encrypt data and move it to cloud storage knowing that only you will be able to decrypt the data on return.
As an extension to the KeyID notion, we also provide interfaces for migrating encrypted data between VMs and through Amazon S3 storage.
Now you are ready to begin.