Administration Model
Contents
Introduction
HyTrust KeyControl supports three distinct administrators, each with distinct privileges. Roles can be combined in any manner. A small organization may have an administrator with all roles. A Cloud Service Provider who manages multiple customers may have different VM Set administrators for different customers: Domain Administrators managing the hardware/storage, and Security administrators who provide oversight. Companies who are using HyTrust KeyControl to manage VMs in the public cloud or other environments may have multiple Cloud administrators, each managing a set of VMs.
The following figure shows the three different administrative roles.
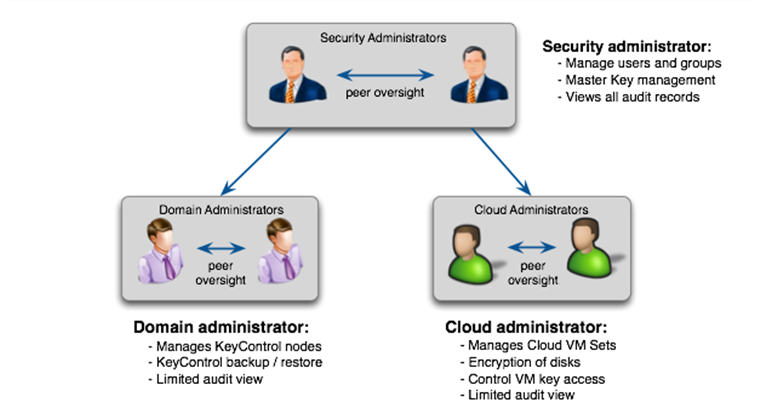
Security Administrators can perform the following tasks:
- Create and delete users.
- Assign / revoke privileges.
- Disable / enable accounts.
- Edit default settings such as the password expiration time, length of passwords, how long accounts are active, and the default time window during which administrators can log on.
- Install the initial and subsequent license keys.
- Restore a KeyControl cluster.
- See all activity in the system but do not see any objects (VMs, storage, encryption keys).
Domain Administrators can perform the following tasks:
- Install and set up new hardware.
- Authenticate new KeyControl servers.
- Manage software updates.
- View system information such as disk usage, dedup effectiveness, CPU load average.
- Create storage pools and filestores.
- Assign access to filestores to specified VM Set groups.
Cloud Administrators can perform the following tasks:
- Create and manage Cloud VM Sets.
- Create certificates associated with a Cloud VM Set, and assign them to VMs.
- Install DataControl agent software on Linux and Windows servers and register the VMs.
- Specify the boot time properties of VMs - do they need to authenticate on boot or not?
- Revoke access to VMs or individual devices resulting in a force unmount of the filesystem and removal of access to the data.
- Create encryption keys (keyIDs) that can be shared with the VMs in the same Cloud VM Set in order to encrypt and decrypt files.
When the system is installed, there is a single user created called secroot, who has all three roles. This is shown below. Each administrative tab at the top of the screen will only be accessible if the administrator has the appropriate privilege.
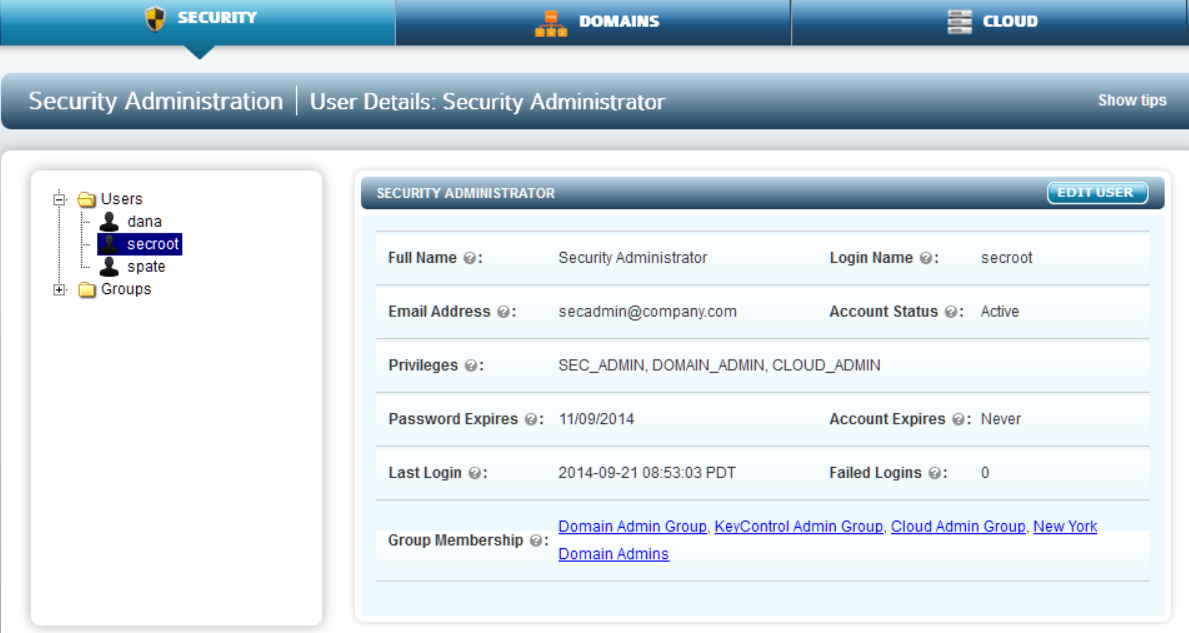
The secroot user cannot be removed but Domain and Cloud Admin privileges can be removed. The name "secroot" can be changed.
Administrative Groups
All objects in a HyTrust environment are owned by groups. For example, storage allocated for Cloud VM Sets is assigned to a Cloud VM Set group rather than an individual user. In multi-tenant systems, having a single user can cause problems if that user has sole access to specific parts of the system and refuses to hand over passwords if the user leaves the company. Having two more users in each group prevents this problem from occurring.
Examples of where groups come into play:
- Alerts are posted to groups.
- Logging / auditing information is visible on a group-by-group basis.
- Each KeyControl appliance is a member of the default KeyControl Admin Group.
- If Cloud VM Sets for different customers require separate administrators, you should create multiple groups and separate the admins into these groups. Each administrator will only get access to VM information that belongs to his or her group.
When the system is installed there are three default groups created, as shown below:
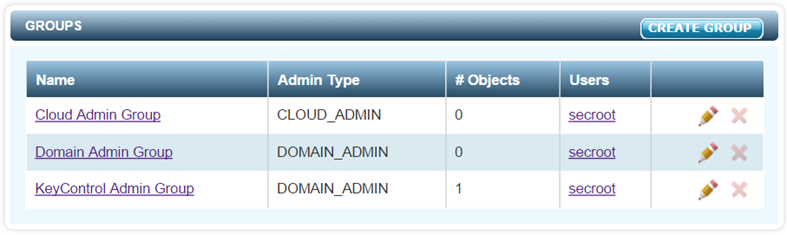
The groups can be changed and additional groups can be created.
- The Cloud Admin Group is used as a container for Cloud VM Sets. When Cloud VM Sets are created they are placed in a Cloud Admin Group. In a multi-tenant environment, unique Cloud Admin Groups will be created for each tenant. Within their respective groups, they can allocated any number of Cloud VM Sets. For example, if Company-A and Company-B are sharing the KeyControl, one could create a Cloud Admin Group called "Company-A VMs" and one called "Company-B VMs." Administrators for Company-A will be placed in the "Company-A VMs" group and administrators for Company-B will be placed in the "Company-B VMs" group. Company-A administrators will not be able to see any objects owned by Company-B and vice-versa.
- The Domain Admin Group is used as the default group for all Domain Administration actions.
- The KeyControl Admin Group is used for all KeyControl cluster operations.
The names of these default groups can be changed easily. Just click on the pencil icon or click on the group name and select EDIT GROUP.
The system is fully functional with just these groups.
