SSH Secrets
You can add Secure Shell (SSH) private keys as secrets to your KeyControl Vault for Secrets. This allows you to access a server via SSH using the secret.
Each SSH secret is set up with a port through which the KeyControl Vault for Secrets proxy connection is established. Please note:
-
The KeyControl Vault for Secrets ensures that two ports are never assigned to the same SSH secret.
-
A KeyControl Vault for Secrets cluster can accommodate up to 6k SSH secrets.
Along with the SSH private key, you define the user and server details. You also define the access policy for the user for the relevant KeyControl Vault for Secrets. When you configure the SSH private key secret, you specify the host (IP), user (on the VM), and you upload the SSH private key (the same private key used to access the VM directly). You can then log on to your KeyControl Vault for Secrets to confirm the details and access the server using the SSH key secret.
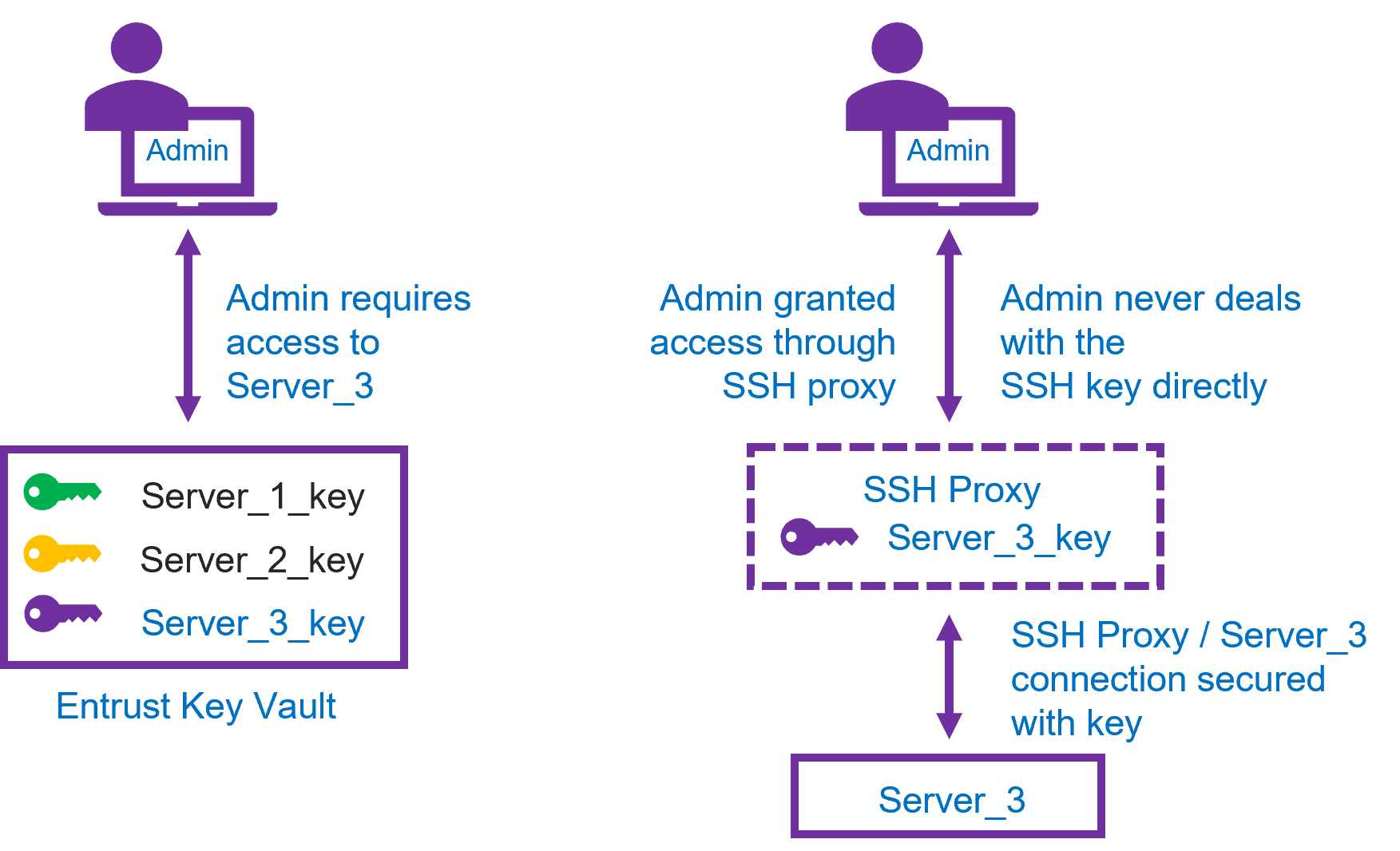
For additional security and to protect important assets, you can restrict access, so it is only possible for the user to access the server using their SSH secret. For example:
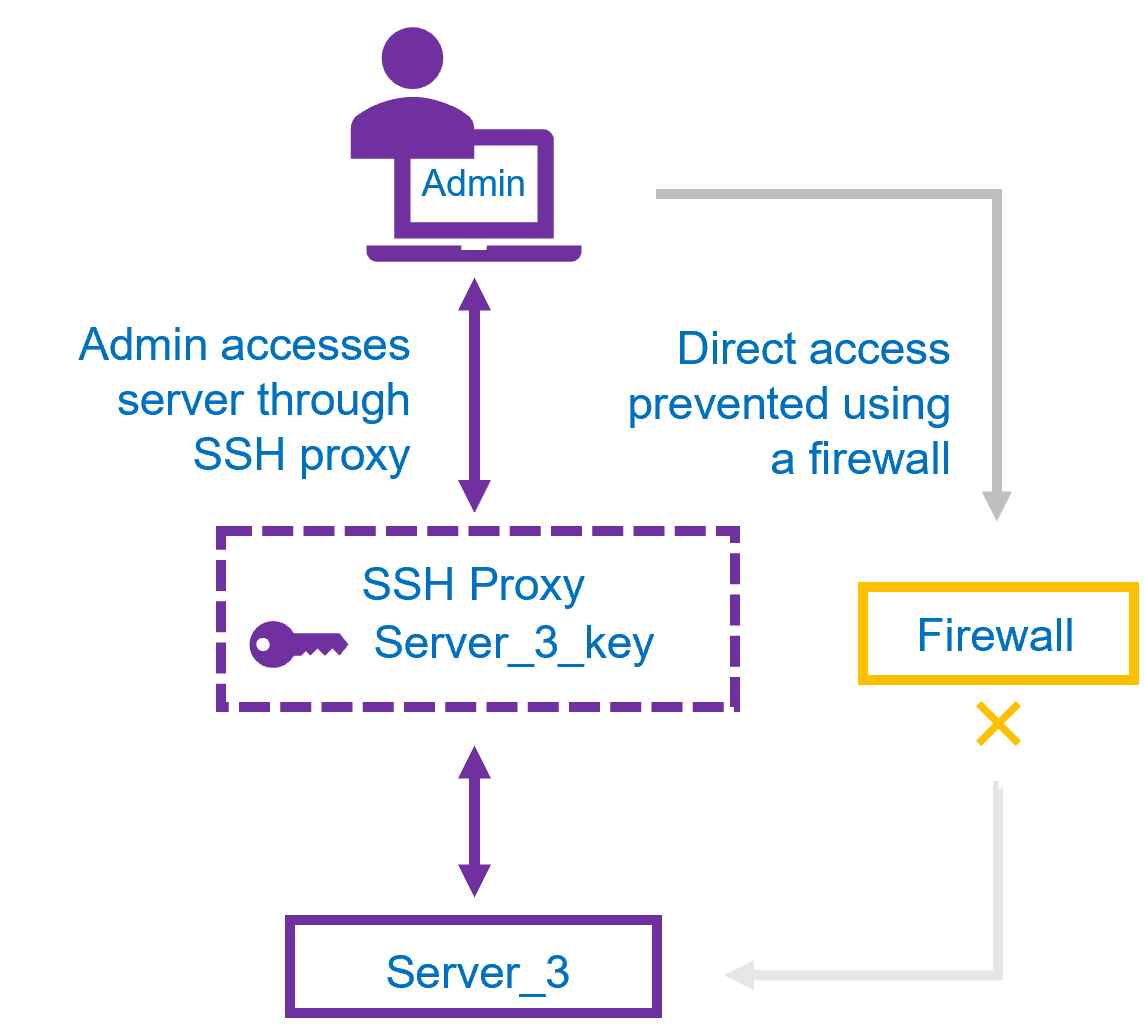
Once configured, users/admins access their VMs using the KeyControl Vault for Secrets. Users log on to their remote VM through their vault, using the vault IP, the vault user name and the port specified in the SSH secret. The port is specific to the VM.
Users with access to many VMs over SSH can log on to all their VMs using their vault IP and vault user name, and simply change the port to specify the VM.
-
For details on creating and configuring SSH secrets, see Creating an SSH Secret.
-
For details on how users log on to remote servers using their SSH secret, see Logging on to remote server using SSH Secret.
