The Boundary Controls feature utilizes Policy Rules and constraints in HyTrust CloudControl® (HTCC) to authenticate and authorize delivery of encryption keys for the data encrypted by HyTrust DataControl and managed by HyTrust KeyControl.
HTCC has fine-grained knowledge of all of the virtual machines in an enterprise. When Boundary Controls are enabled, HTCC coordinates with KeyControl to ensure that policy-based boundaries are maintained in that enterprise. Examples include:
This combination of two of HyTrust’s products responds to these needs by leveraging the capabilities of each product.
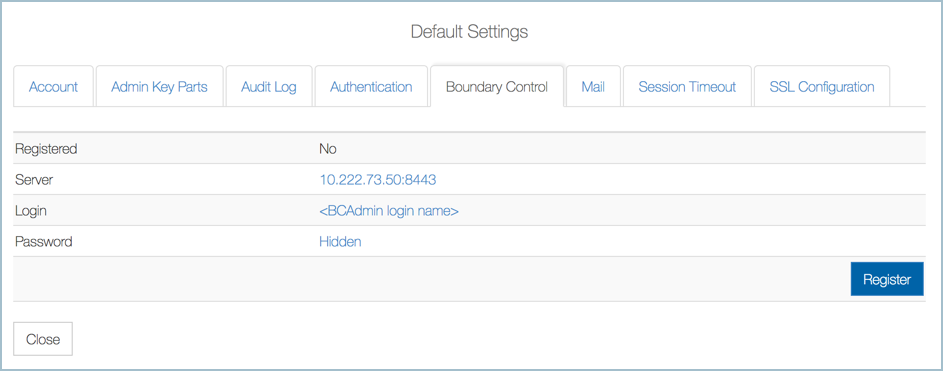
To enable Boundary Controls in HyTrust DataControl, click the Settings Icon and then click Boundary Controls. The Default Settings dialog box opens to the Boundary Control tab. Enter the requested information into the following form, and then click Register.

Details of the Boundary Control tab:
All virtual machines are configured as part of Cloud VM Sets. When VM Sets are created, you must decide at that point whether or not you want Boundary Controls enabled on each one. Once the VM Set has been created, you cannot change the Boundary Controls setting that was originally configured.
| Note: | You must have VMware Tools installed on each VM before you can enable Boundary Controls. In most cases, this is already done, but in some cases, including CentOS 7, you need to explicitly install VMware Tools. |
For more information on Boundary Controls, see the HyTrust CloudControl Documentation.
For more information on VM Set creation, see Overview of Cloud Operations and VM Sets.