KeyControl Backup and Restore
Contents
- Introduction
- Backing up the KeyControl Cluster
- How Often to Back Up the KeyControl cluster
- Restoring from a KeyControl Backup Image
Introduction
The object store on each KeyControl node is identical and therefore backup needs only to take place from a single KeyControl node. A restore operation must be performed on a single node. Only after restore can additional nodes be added to reconstruct the cluster.
Keys, policies and other information within each KeyControl node is encrypted. At the top of the KeyControl key hierarchy is the Admin Key, which must be carefully protected. To protect the Admin Key, we provide an "n of m" Admin Key backup model. The Admin Key is split into "m" pieces where "m" is the number of security administrators. Each administrator is given part of the key and to reinstate the Admin Key, "n" of the "m" administrators must be present to enter their part of the key. Note that the admins are not given part of the actual key itself but a mathematical representation of part of the key.
Consider the following figure:
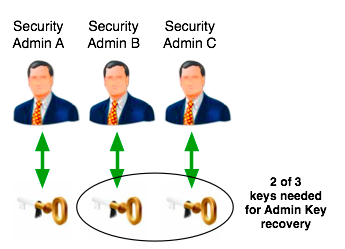
In this example there are three security administrators and each is given a key part. We choose the value of "n" such that 1 <= n <= m. In this example, the value of "n" is "2". When restoring the Admin Key, any two of the admins need to be present. This is covered by one of the following combinations:
- Security Admin A and Security Admin B
- Security Admin A and Security Admin C
- Security Admin B and Security Admin C
Admin Key parts are generated under the following conditions:
- During installation of the first KeyControl node. In this case, the secroot admin gets the only part.
- A security admin is added or deleted. After one of these operations, key parts are generated again.
- You decide to explicitly generate new key parts.
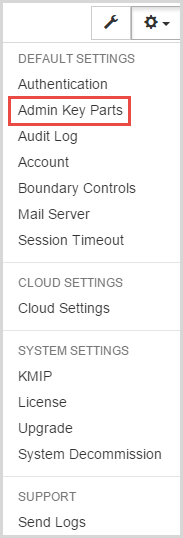
If you wish to generate the Admin Key parts n, from the Settings Icon, click Admin Key Parts, as shown below:
You then see the Default Settings dialog box, open to the Admin Key Parts tab.
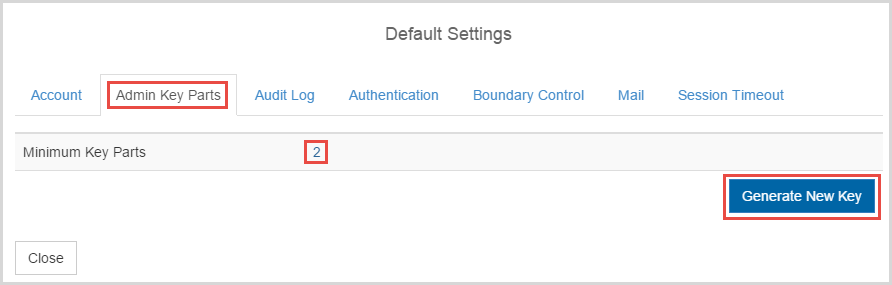
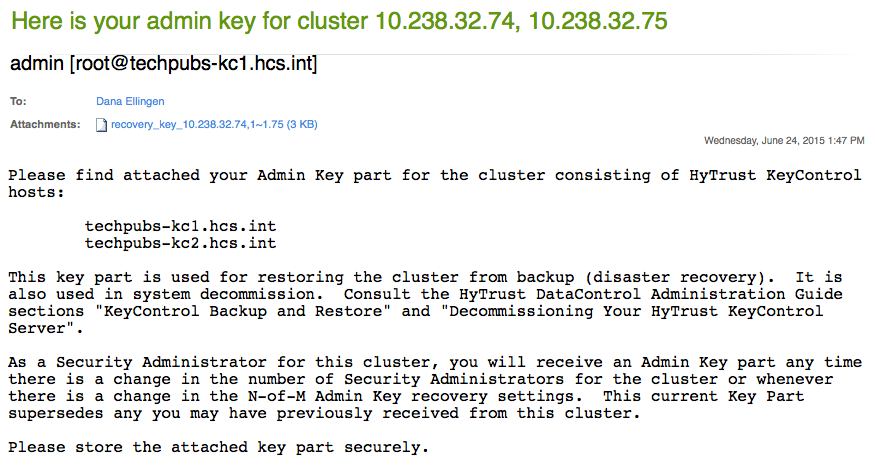
Enter the Minimum Key Parts (the value of "n") and click Generate New Key. Each security administrator will receive a key part as an alert, and in email (if you enabled email). For example, below is a screen shot of one of the emails received. Note that the key part appears as an attachment:
If you disabled email access on first GUI login, Admin Key parts will be sent as alerts only. Each security administrator will be able to locate their key part by clicking Alerts Icon, the right-most icon at the top of the screen. Select the alert that begins “Here is your Admin Key...”
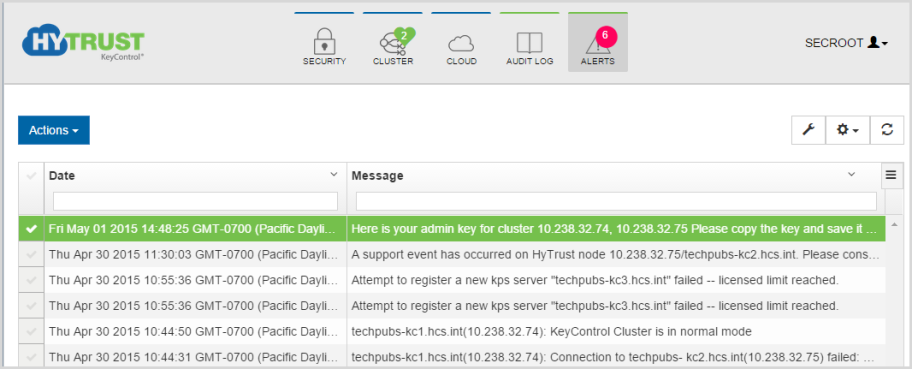
and the details screen for this alert shows your key part as follows:
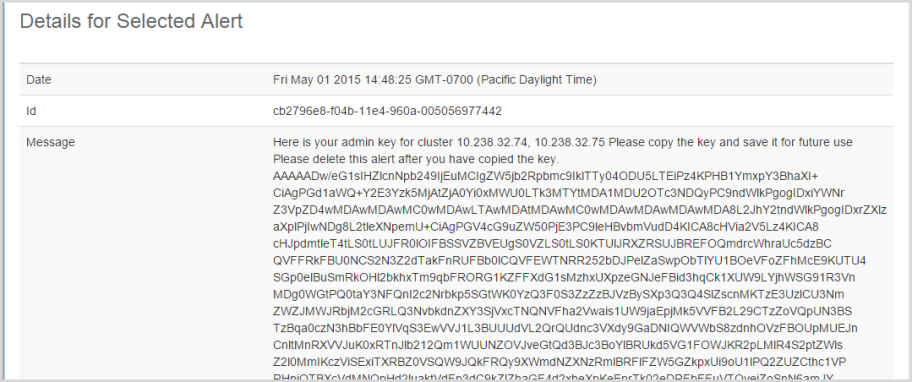
Note that you will see an alert when first logging into the GUI or when generating key parts either directly or by adding or removing security administrators.
It is vital that these key parts are stored securely. If "n" pieces are not available, restore of a KeyControl node will not be possible. Note however, that a new Admin Key can be generated at any time up to the point of KeyControl backup/restore.
NOTE: Admin Keys are generated automatically any time a new Security Administrator is created, broken into an appropriate number of key parts and distributed one per Security Administrator. Admin Keys can also be generated on demand, by clicking the Settings icon, then Admin Key Parts, and then Generate New Key. It is generally a good idea to generate new keys just prior to running a backup.
Important: Be sure that your Security Admins keep and protect their Admin Key Parts, because they might well need something other than the latest.
When restoring from backup you must use the right key parts. For example, consider the following scenario:
| Time | Action | Key Parts |
|---|---|---|
| t0 | security admin added | key parts K1 generated |
| t1 | backup taken | |
| t2 | security admin deleted | key parts K2 generated |
If you restore from the backup taken at time t1 and admin key recovery is required, you will need to use the “K1” key parts.
Backing Up the KeyControl Cluster
Now that key parts have been distributed, the Domain Administrator needs to set up access to the KeyControl backups, all of which are securely encrypted.
The default KeyControl backup settings can be set by selecting the Clusters Icon and entering the appropriate IP address in the Backup Hosts field:
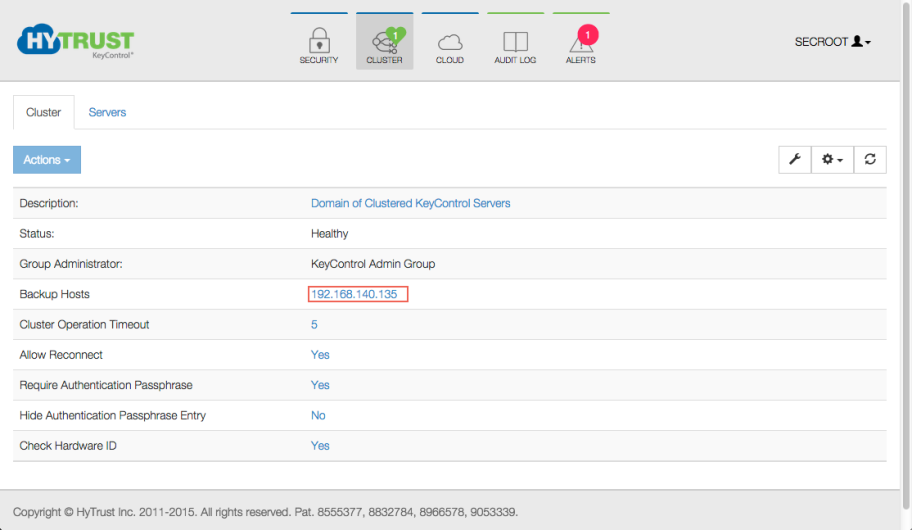
Enter a list of hostname / IP addresses, separated by commas or spaces, for nodes that you want to be able to access the backups. Note that you can add 0.0.0.0, which although not totally secure, enables backups from any client. Of course, you would still need to present the appropriate n of m keyparts.
From one of the specified nodes, you can now mount the exported filesystem as follows:
# mount -t nfs 192.168.140.135:/hcs/backup /backup # ls -l /backup total 506 -rw-r--r-- 2 root wheel 129536 Aug 18 17:28 hcs-kps-2011-08-19-00:28:23.bu -rw-r--r-- 2 root wheel 129536 Aug 18 17:28 hcs-kps.bu
Note that you can mount the filesystem from any KeyControl node in the cluster.
How Often to Back Up the KeyControl cluster
KeyControl backup images are typically very small. We snapshot the KeyControl object store (the place where keys, policies and configuration data is stored) each time a change is made. For example, every time a key is allocated, a new snapshot is taken. The size of the KeyControl backup image will depend on the number of HyTrust DataControl Policy Agents, users, keys and other such information. To give you some idea of the size, here we view the available backups for a minimally used system:
# ls -l /mnt total 517 -rw-r--r-- 2 root wheel 159232 Feb 12 10:06 hcs-kps-2014-02-12-18:06:21.bu -rw-r--r-- 2 root wheel 159232 Feb 12 10:06 hcs-kps.bu
As shown above, this system is only approximately 160 KB in size. We recommend that you back up often and monitor the sizes as your KeyControl usage increases.
Restoring from a KeyControl Backup Image
Restoring from a KeyControl backup will only need to be performed if there is a catastrophic failure in the KeyControl cluster. If one KeyControl node becomes unusable, for example due to hardware failures, simply remove the node from the cluster and add a new node.
Note: A full restore can only be done from an ISO image, following the same procedure as you did for installation, shown here: KeyControl Installation from an ISO Image
When restoring a KeyControl node there are two possible scenarios:
- You are restoring to an node that was previously used in the cluster (that is, it has the same hardware ID and no hardware components have changed). In this case, you will not need to perform Admin Key recovery.
- You are restoring to new hardware, which will involve Admin Key recovery.
In either case, you will follow the same procedure for restore as you did for installation.
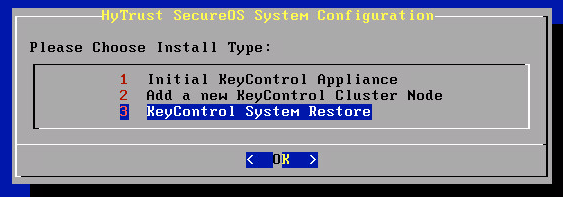
First of all, click OK to install the software.
Once the install is complete and the system reboots, you will then have the option to restore a KeyControl node from backup as the following screen shows:
You enter the root password, set up networking, and then you are prompted to supply the KeyControl backup image from which you want to restore:
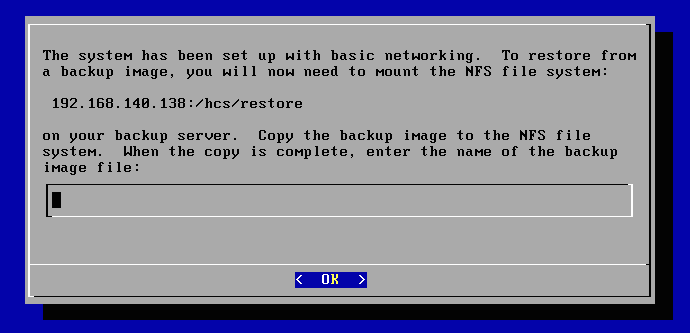
Mount the exported filesystem and copy in the KeyControl backup image as follows:
# mount -t nfs 192.168.140.138:/hcs/restore /restore # cp hcs-kps.bu /restore # umount /restore
At this point, in the installation menu, enter the name of the file you copied in above and press Enter. The restore process now starts. The length of time will be dependent upon the size of the image being restored. Once complete, you will see the "Congratulations!" message and be able to proceed to log on through the webGUI.
At this point there are two things that can happen:
- You have restored to a system with identical hardware. In case we detect that the hardware has not changed and you will be able to log on as you usually do.
- The hardware has changed and you will be prompted by the Admin Key recovery screen, as
shown below.
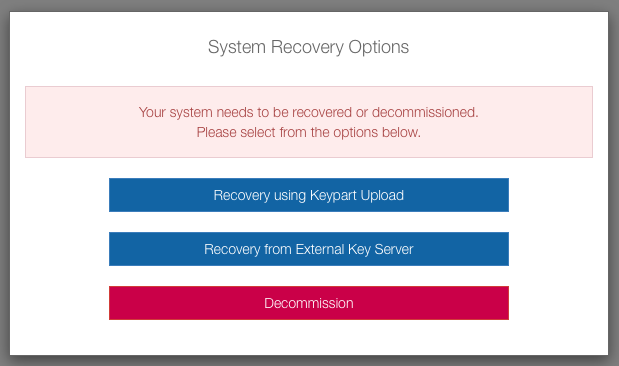
You must now enter the appropriate number of key parts that were generated. Refer to the start of this chapter for further information on generating key parts.
Admin Key recovery can also be done from a KMIP server. For details, see Using the Key Management Interoperability Protocol.
Once you have entered all the appropriate key parts, the system will restart services. You will see a message as the system restarts. Please wait for approximately 30 seconds and refresh your browser. You should then see the login screen appear.