Encrypting Windows boot drives
Contents
- Introduction
- Requirements
- Setup and encryption of the boot partition
- Step 1 - Install the HyTrust Agent
- Step 2 - Register the Hytrust Agent
- Step 3 - Create a separate boot partition
- Step 4 - Install the HyTrust boot agent
- Step 5 - Encrypt the Windows boot partition
- The Boot Process
Introduction
In addition to encrypting regular Windows data partitions, you can also encrypt your Windows boot disk (C:\). Note that HyTrust does not support dual booting. Encrypting the boot partition, in addition to data partitions, ensures that clear-text data never leaves the VM on its way to storage. This prevents virtualization and storage admins from being able to view the data.
The HyTrust Bootloader for Windows is a tool that can be used to encrypt the Windows boot partition using keys that are retrieved, as needed, from the HyTrust KeyControl server. This means that keys are not kept with the encrypted boot partition, thus providing an extra layer of security.
There are a number of steps required to set up your Windows system for boot drive encryption. If you are running within a virtual infrastructure, we recommend that you go through this process once and set up a template VM from which new VMs can be created.
Requirements
The supported versions of Windows for the HyTrust Bootloader for Windows include:
- Windows 7
- Windows 2008
- Windows 2012 (coming soon)
This product will work with and without Service pack 1 installed.
A small bit of extra storage will be required to contain the Windows boot agent and the configuration files necessary to retrieve keys from the KeyControl server. The storage is an extra partition which must be formatted with the FAT32 file system. The partition must be at least 150 megabytes.
Additional notes:
- The encrypted root partition must be on the Windows
C:\drive. Although Windows itself can boot from alternate drive letters, the HyTrust Bootloader is limited to theC:\drive only. - This release will not be able to boot a partially encrypted root filesystem. The encryption process must be completed in order to successfully boot. Therefore, it is highly advisable to back up the VM before beginning to encrypt it.
Setup and encryption of the boot partition
The installation of the components necessary to boot an encrypted version of Windows is a five-step process.
Step 1 - Install the HyTrust Agent
First, you must install the HyTrust agent software on Windows. You must reboot the Virtual Machine before the agent is activated. For installation instructions, please refer to the "Encryption Within Windows Virtual Machines" chapter.Step 2 - Register the HyTrust Agent
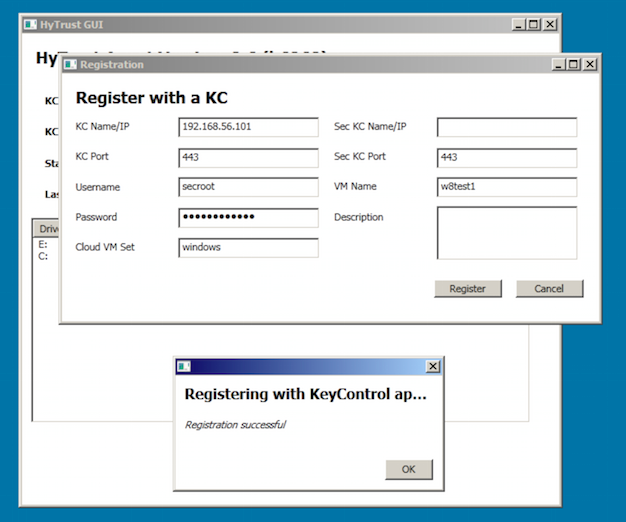
Next, you need to register the HyTrust agent with KeyControl. As shown below, make sure that registration is successful.
Step 3 - Create a separate boot partition
Allocate and format the partition used to contain the boot encryption agent. The typical way that this is done is to add a secondary disk to the virtual machine. The disk can be as small as 150 megabytes. Boot the virtual machine and use the diskmgr tool to create a volume on the new disk. The volume must be formatted with the FAT32 file system. If this step is not done correctly, step 4 will fail. When complete, shut down the Windows virtual machine.
Step 4 - Install the HyTrust boot agent
Install the HyTrust Boot Agent. This is an additional component that must be downloaded separately from the HyTrust Windows Agent. The software cannot be installed from within Windows. The virtual machine must configured to boot from the HyTrust Boot Agent CD and the CD must be inserted in to the virtual machine CD drive.
When the CD boots, the following screen appears:
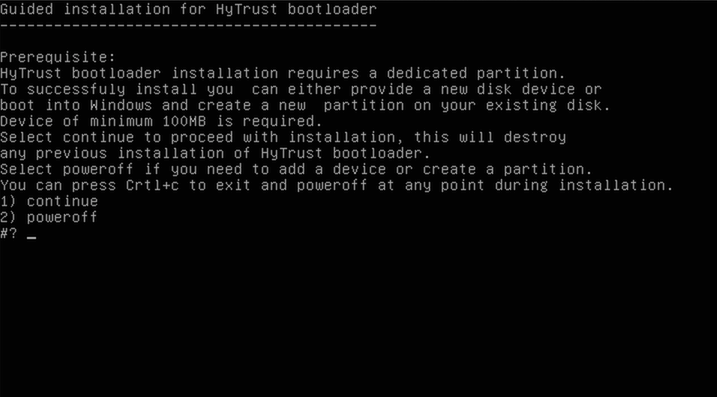
Select option "1" to proceed with the installation. If you have forgotten to add the FAT32 partition in Windows, then select option 2 to power down the VM, disconnect the CD and restart the VM / process.
After selecting option 1 to continue, you will see a list of devices similar to the following:
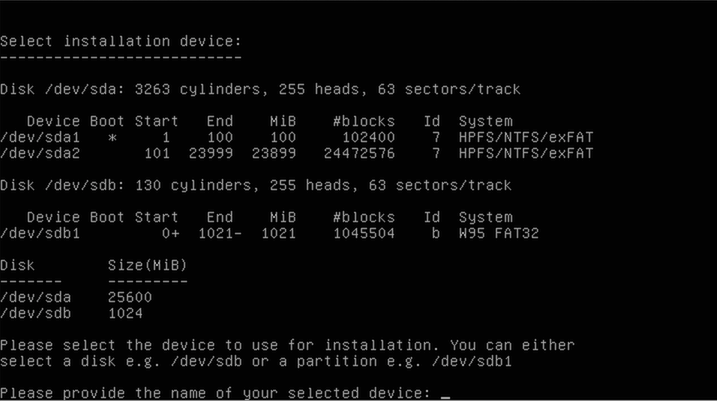
The first step in the installation is to configure the location of the FAT32 partition. A list of partitions that are available is presented. Notice that only one of them is marked as W95 FAT32. The necessary device name is in the first column. Enter that device name. In this instance, we will enter /dev/sdb1.
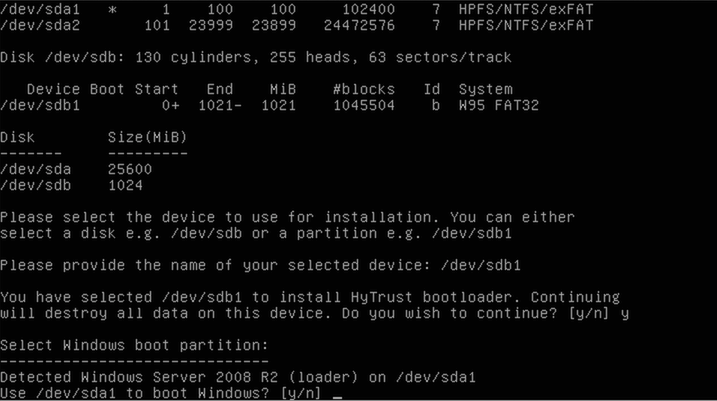
The next item to configure the location of the Windows boot partition. This is not the same partition as the Windows root (C:\). Note that the Windows boot partition is always smaller than the actual root C:\ drive.
The installer will present the partition that it has discovered is the most likely one. Confirm that choice here or enter another.
Note that you can see the distinction between the Windows boot partition and the root partition by running the Windows diskmgr utility. For example:
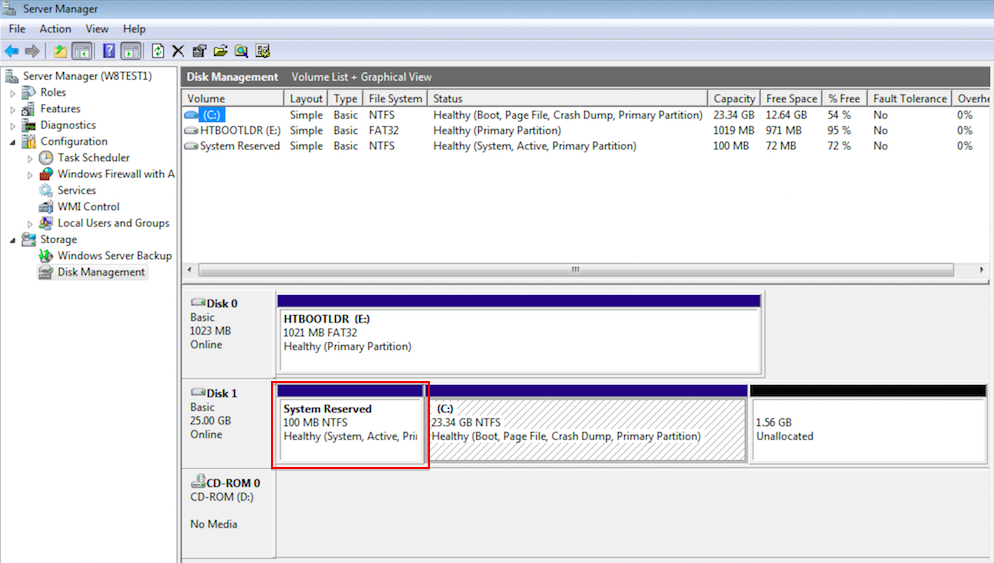
The small boot partition is listed as System Reserved. No part of the Windows root C:\ is ever decrypted on disk and the boot partition contains only a small part of the bootstrap process.
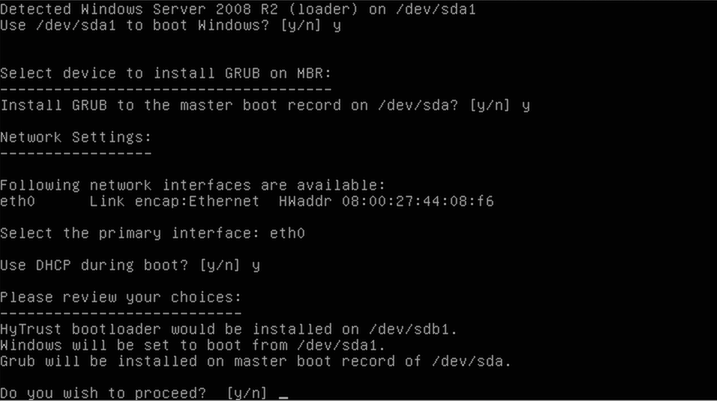
The next step simply confirms that you want to make these choices permanent and configure the virtual machine to boot using the HyTrust bootloader.
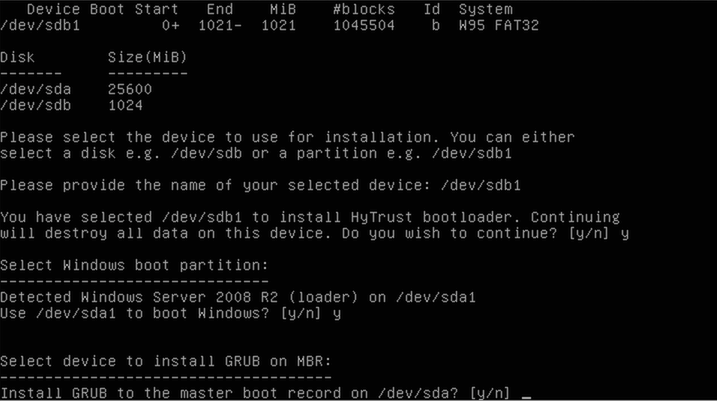
You must now configure the network that will be used to contact the KeyControl server. If you have multiple NICs configured, you will be presented with a list to choose from. Otherwise, you will be asked to confirm the one that has been chosen. You must make sure that whatever NIC is selected will be able to contact the KeyControl server.
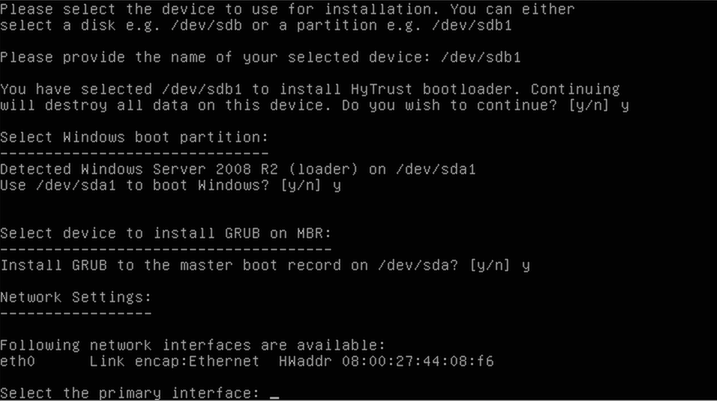
The last configuration item will select the networking parameters needed to configure the chosen NIC. You will be able to configure the IP address, netmask, gateway, and DNS server.
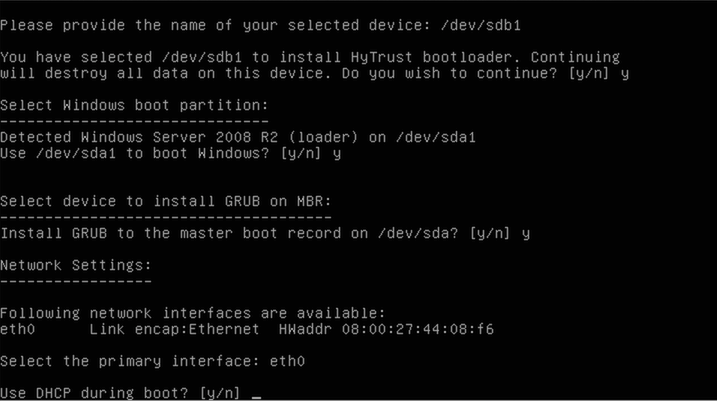
Finally, confirm the settings from above. The configuration data will be permanently stored. The CD will be ejected and the virtual machine will be shut down.
At his point, you no longer need the CD. You will never be asked to boot from it again, except to update HyTrust Bootloader software, or to reconfigure the bootloader. It is not needed to boot the encrypted Windows partition after the installation is complete.
Step 5 - Encrypt the Windows boot partition
Next you need to encrypt the Windows root C:\ drive. The completed installation of the HyTrust Bootloader will shut down the virtual machine. When it is powered back up, it will boot in to Windows. At that point, the C:\ drive can be encrypted. Note that the HyTrust GUI will not allow the C:\ drive to be encrypted until the HyTrust Bootloader is successfully installed.
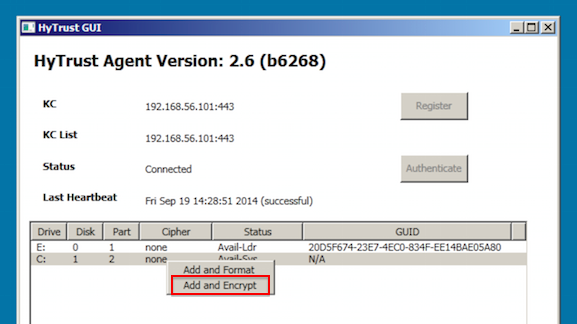
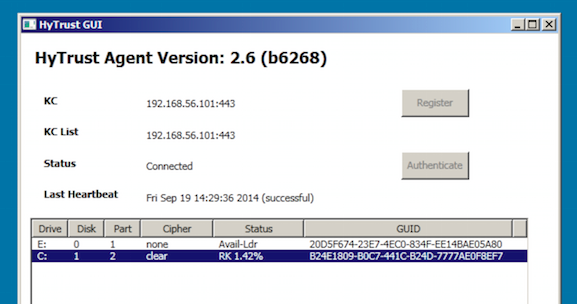
When it has started encrypting the C:\ drive, the process will be displayed in the HyTrust GUI. When complete, the status will change to Attachedť. At that point, the encryption process is complete and the VM can be safely shut down or rebooted.
The Boot Process
HyTrust Bootloader for Windows uses a small pre-boot environment to retrieve encryption keys for the boot device each time the system starts up. The encryption key is never stored on the system itself. Rather, the system is reconfigured to boot the HyTrust Bootloader before trying to to boot Windows. The Bootloader retrieves the key from KeyControl and then supplies it to the secondary stage which will boot Windows. Keys are only ever stored on the remote KeyControl server.
Normal Bootstrap
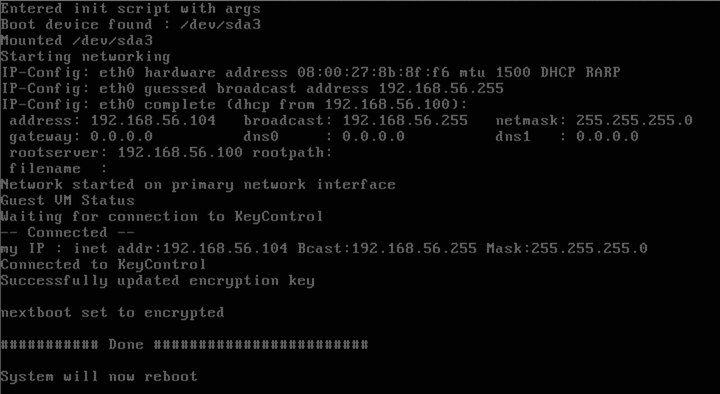
In the following screenshot, you can see the operation of the HyTrust Bootloader for Windows. It indicates that it has successfully contacted the KeyControl server, presented credentials that allow it to retrieve the boot partition encryption key, and retrieved the key. When complete, it will once again reboot, this time in to Windows.
Failure to retrieve keys when booting
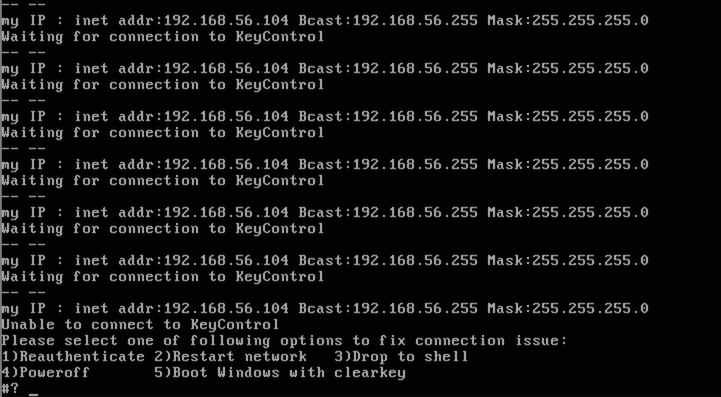
Since encryption keys are never stored locally, a VM will require access to the KeyControl server when booting. Failure to contact the server will prevent the system from booting. If the KeyControl server is not available when the system is booted, it will repeatedly attempt to contact it until finally presents a console menu which allows a number of options. They are:
- 1. Re-authenticate the VM. If for any reason the credentials of the VM become stale, then it must be re-authenticated to the KeyControl server in much the same way as a running VM would have to do. Possible reasons why this might occur include the grace period expiring. This option will allow the credentials to be re-entered. Key retrieval will proceed after this.
- 2. Restart the network. This option instructs the VM to reattempt to contact the KeyControl server and once again retrieve the encryption key. If no selection is made in this menu after 30 seconds, then this option will be taken automatically.
- 3. Drop into a recovery shell. Provides a simple recovery shell.
- 4. Power the VM off.
- 5. Boot into Windows without a key. The only time this option would be useful is before the boot partition has been encrypted. It instructs the Bootloader to boot without an encryption key.
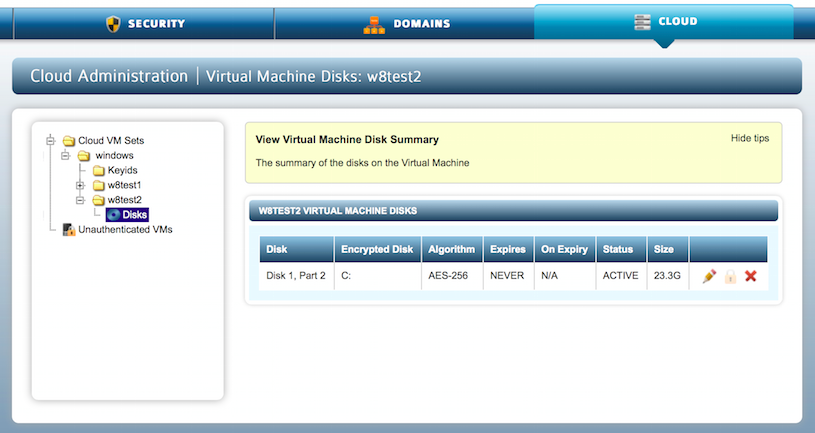
Key Management
One of the important features offered by this system is the ability to remotely control access to the encrypted data from the KeyControl console. HyTrust Boot Encryption also offers this feature. The boot partition is presented in the KeyControl GUI as simply another disk to be managed. Keys can be revoked and access granted in the same manner as non-root disks.
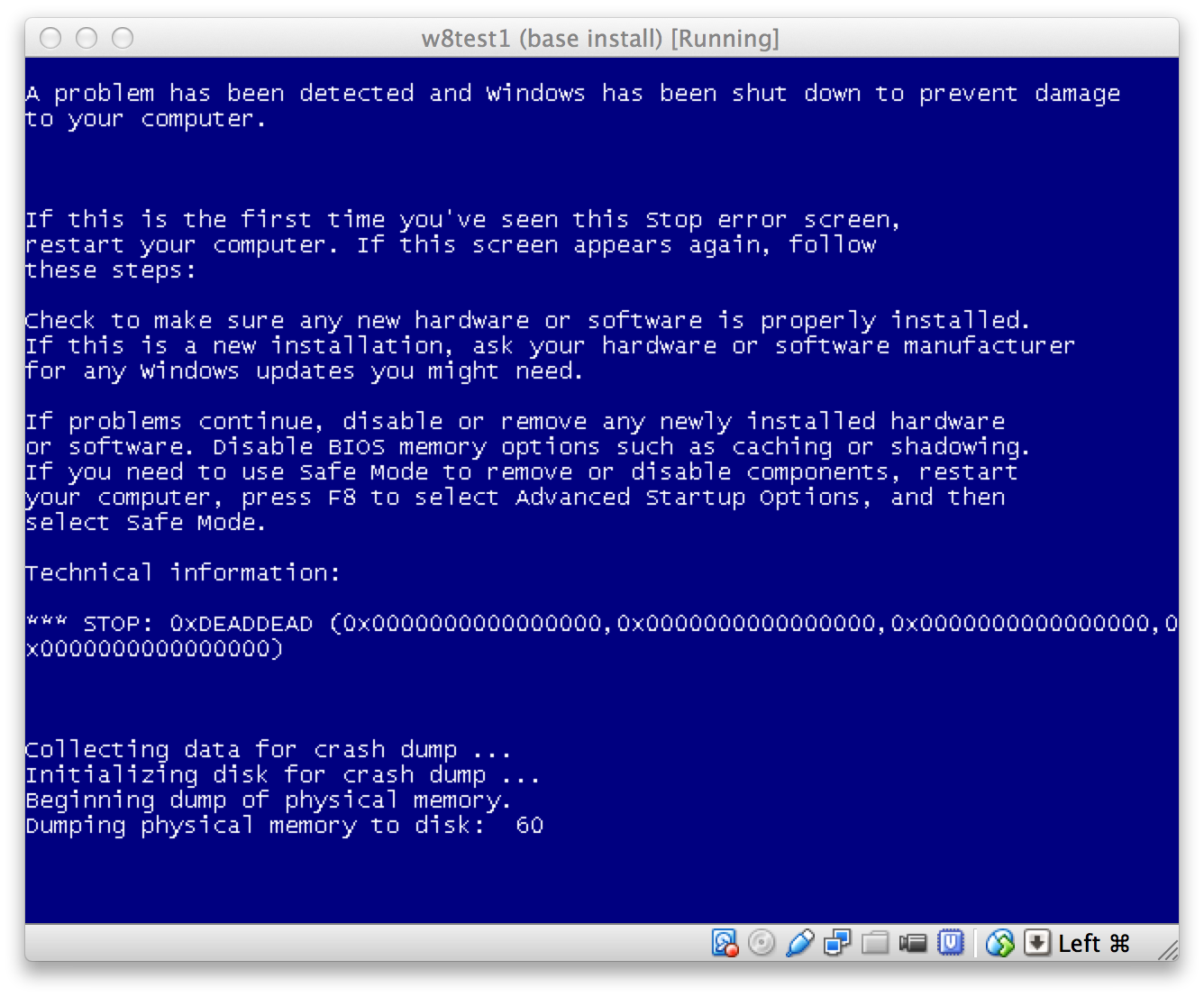
If access to the boot encryption key is revoked, the HyTrust Encryption Agent for Windows will immediately, upon receiving the next heartbeat from the KeyControl server, cause the VM to BSOD (Blue Screen Of Death) since I/O is no longer permitted. The BSOD status code will be set to the value “DEADDEAD” so that it can be quickly determined that a key revocation was the reason for the BSOD.
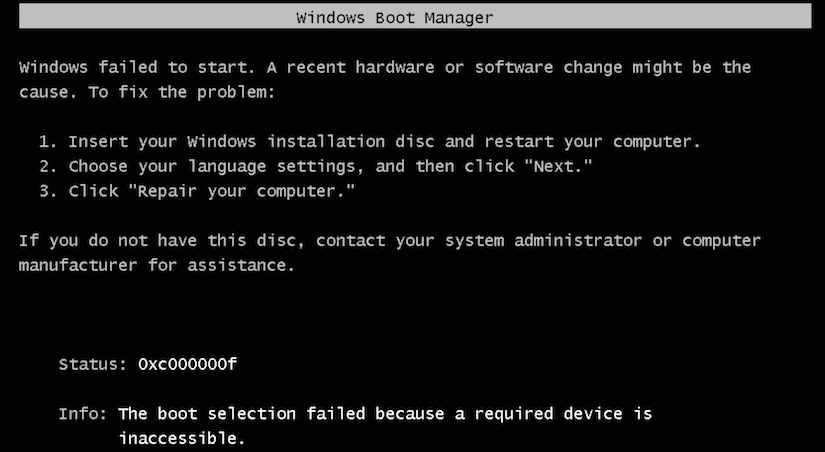
The BSOD will eventually result in the VM rebooting. Of course, at this time, the key is no longer available, since access has been revoked. Key retrieval will fail, causing the VM to attempt to boot Windows without a key. In the following screenshot you can see that the bootloader was unable to fetch keys.

Windows will now fail to boot since the encryption key cannot be retrieved. Thus, when it attempts to boot, it will fail with the status code 0xC00000f, indicating a failure to read the disk. This is shown in the screenshot below. Subsequent boot attempts after the key access is granted will not result in this error.
Attempts to boot the fail will fail until the VM is once again granted access to the encryption key. At that point, restarting the VM will once again proceed normally. The encryption key will be retrieved and passed to the Windows bootloader allowing the VM to operate normally.

