Product Architecture, Features and Terminology
Contents
- Introduction
- HyTrust KeyControl / DataControl Product Features
- HyTrust SecureOS
- HyTrust KeyControl Cluster
- WebGUI Administrative Interface
- Application Programming Interface
- Administration model
- Key management capabilities
- Secure authentication of new nodes
- Secure protocol support between nodes
- Support for VM in-guest encryption using the DataControl Agent
- Secure data migration
Introduction
In this section we cover the architecture of the HyTrust KeyControl (HTKC) and HyTrust DataControl (HTDC) solution, describe the main features of the product and cover terminology that will be used throughout the Administration Guide.
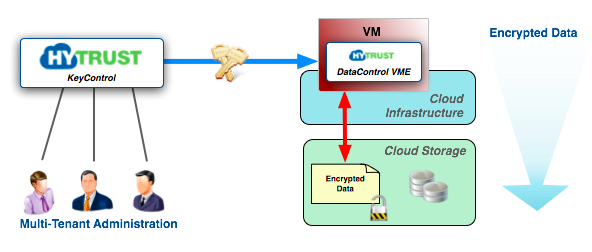
The following figure provides a high level view of the main architectural components of the HyTrust KeyControl and DataControl solution.
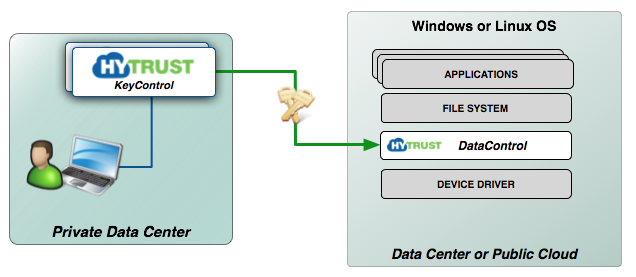
HyTrust provides encryption and key management for virtual and physical machines. The major components of the HyTrust solution are:
- HyTrust KeyControl - supporting an active-active cluster, the KeyControl cluster stores keys, policies and configuration data related to the cluster, or any number of virtual machines where the DataControl agent is installed. Administration of the system is through a web-browser-based GUI or through a set of REST-based APIs. Communications between the browser and the KeyControl cluster is over HTTPS. Since this is a full active-active cluster, the browser can point at any KeyControl node in the cluster. Any changes made are immediately reflected on all cluster nodes.
- HyTrust DataControl - an agent that runs inside Windows and Linux virtual machines providing encryption of virtual disks and individual files. The DataControl agent is typically used to provide encryption within any public Cloud environment, although one can provide encryption of virtual machines (or physical servers) in the data center. All VMs that have the DataControl agent installed can also securely share encrypted files. Encryption keys (keyIDs) can be used by selected VMs to encrypt and decrypt files. Encrypted files can also be sent to cloud storage such as Amazon S3 and only accessed by the selected VMs where the DataControl agent is installed.
The KeyControl appliances contain the HyTrust SecureOS as the core operating system.
HyTrust KeyControl / DataControl Product Features
This section lists the features of HyTrust KeyControl / DataControl solutions.
HyTrust SecureOS
The base of every KeyControl appliance is the HyTrust SecureOS, a light-weight, locked-down operating system that has no runtime login/SSH access to the system, to prevent tampering or attempts to access clear-text data and/or encryption keys. Each KeyControl appliance can be installed as a virtual machine or can be installed on physical (x86-based) hardware.
The main features of SecureOS are:
- A locked-down, hardened operating system.
- An ISO, OVA or AMI image that supports installation of a KeyControl appliance (HTKC) from which the DataControl agent (HTDC) can be downloaded.
- Mirrored root partitions for HCS software provides high availability, preventing downtime from disk failures.
- Encryption of the HyTrust software on the installation media to prevent tampering.
- No general login/SSH access to the KeyControl appliance, preventing key snooping or clear-text data snooping.
- Minimal OS software installed with industry standard lock-down capabilities built in.
- Ability to extract debug information through secure login. Login access does not give access to the main running system, so that there is no access to any sensitive data or encryption keys.
- GUI-based extraction of log / support information.
- Built-in VMtools supporting the management tools and vmxnet2 adapter.
HyTrust KeyControl Cluster
At the heart of every system is an active-active cluster of KeyControl servers that manage encryption within individual virtual/physical machines. All administration takes place from a standard web browser to any node in the KeyControl cluster or from a set of REST-based APIs. KeyControl servers typically reside in your data center but could be run out of the public cloud as well.
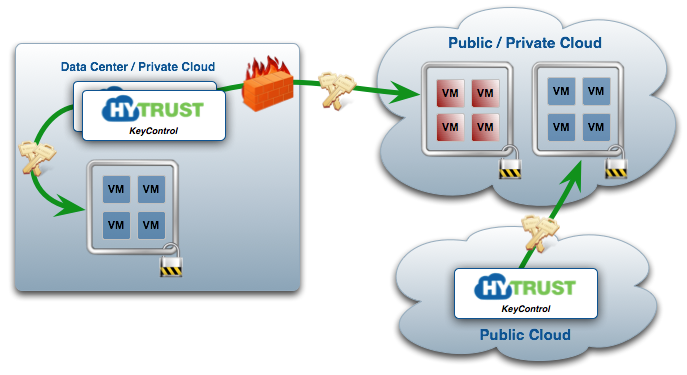
KeyControl features include:
- Full active-active cluster.
- Clustered object store protecting keys, policies and configuration data. All objects are encrypted and ultimately wrapped with a Master Key.
- Master Key protection utilizing a software-based "n of m" backup. The master Key utilizes a hardware-based signature. This prevents KeyControl backups from being stolen and installed on new hardware.
- Mirrored system drives to protect against disk failure.
- Node join / leave without affecting the ability to deliver encryption keys.
- System moves into degraded mode (read only) on network disconnect or KeyControl failure. While in degraded mode, any KeyControl node can still serve requests for keys and policies from VMs where the DataControl agent is installed.
- Each DataControl agent talks to any KeyControl cluster node switching between them if they detect a KeyControl node to be down.
- Support for local authentication or RADIUS.
- Support for environments with and without email access.
- Strict password controls / checking.
- Rich RESTful API.
WebGUI Administrative Interface
Administration of the system takes place through the "webGUI," an administration console accessible through a standard web browser.
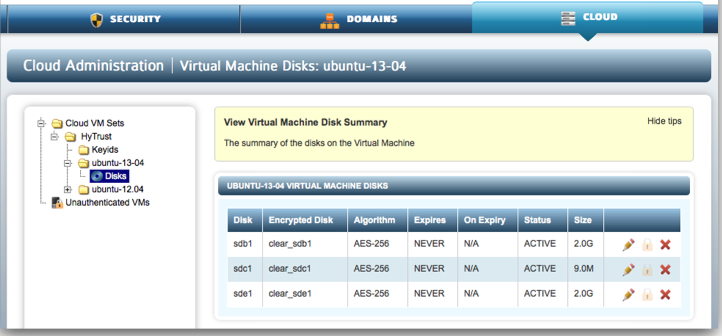
Access to the webGUI is over HTTPS and works with the standard browsers (tested with Safari, Internet Explorer, Chrome and Firefox). The full administration guide is accessible by clicking Help at the top right of the screen.
Application Programming Interface
In addition to the webGUI interface we also provide a set of REST-based APIs and a Python script (that wraps the API calls and talks to the VMs for provisioning) to allow you to programmatically manage users and groups within the KeyControl cluster and also manage encryption within virtual machines.
Administration model
The HyTrust solution provides a rich administrative framework that spans multiple organizations of different sizes from the single administrator IT shop to a large, multi-tenant cloud service provider who needs to support secure customer environments.
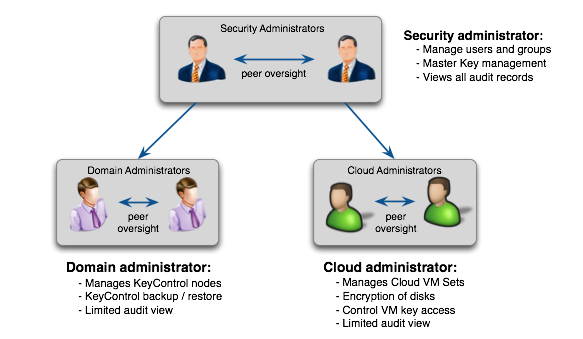
The administration model provides for:
- Multi-tenancy. Administrative roles allow for need-to-know and separation of duties. There are three distinct administrators (Security, Domain, and Cloud). Roles can be combined and there are no limits to the number of administrators. Administrators can be placed in administrative groups to provide peer oversight. All objects in the system are owned by administrative groups and not by administrators.
- Support for multiple roles per admin.
- Keys are never exposed through the webGUI or any other mechanism.
- Alerts through the webGUI and through email.
- Audit records which can be displayed in the webGUI, saved to local disk or exported through syslog to an external log server.
- Security Admin:
- Can create / delete users / groups, assign users to groups.
Groups allow for dual knowledge (no single person can cause havoc by withholding information).
- Cannot see any storage, policies, virtual machines or modify anything.
- Sees all audit records. These records can be exported to an external syslog server.
- Domain Admin:
- Sets up virtual HyTrust machines - the KeyControl Cluster. KeyControl is typically set up as an active-active cluster to protect against system failure.
- Only sees audit records based on his / her group actions.
- Cloud Admin:
- Manages sets of virtual machines where the DataControl agent is located providing encrypted devices. Capabilities provided for this role are:
- Create and manage multiple "Cloud VM Sets," logical groupings of virtual machines, for example, "VMs running in AWS" or "VMs running in Savvis".
- Create certificates for VMs which specify how long keys will be delivered for.
- Specify key expiration dates.
- Revoke access to individual encrypted devices or the whole VM. When devices are revoked, filesystems are forcibly unmounted, thus removing access to clear-text data.
- Creatie encryption keys to securely move encrypted data between specified VMs.
- Only sees audit records based on his or her group actions.
Key management capabilities
Key management is often referred to as the "Achilles heel of encryption." Managing encryption keys can be painful and makes encryption difficult to deploy and fearful for many organizations. HyTrust KeyControl provides strong encryption technology without the need for users to be experts on key management. Wherever possible, the internals of key management are hidden from the user.
For a KeyControl/DataControl combination:
- AES 128/256-bit encryption support (CBC and XTS cipher modes).
- Automatic detection and use of hardware crypto - AES-NI on Intel and AMD processors.
- Set an expiration date for keys - we generate one key per device.
- Secure encrypted communication between KeyControl clusters and DataControl agents.
- Ability to cache keys on the client VM (encrypted with a passphrase).
- Ability to clone VMs and authenticate VMs (for backup, restore, autoscaling and DR purposes).
- Share encryption keys between VMs in the same Cloud VM Set, which allows these VMs to encrypt, securely transport, and decrypt data.
- On-line key rotation on Windows and off-line rekey on Linux.
For details on the processors that support AES-NI, please view this website.
Secure authentication of new nodes
Any new nodes (KeyControl server or VMs using DataControl) added to the system must be authenticated. As part of install, a passphrase is required on the node to be added and then on a KeyControl node within the cluster. This one-time passphrase allows the system to establish a secure channel over which certificates are exchanged allowing for secure subsequent communications.
Secure protocol support between nodes
The HyTrust solution provides secure communications between all nodes in the system:
- Secure REST-based protocol over HTTPS
- Used for all KeyControl-KeyControl and KeyControl-DataControl interactions
- All sensitive information (keys, policies) wrapped for additional security
Support for VM in-guest encryption using the DataControl agent
The HyTrust DataControl agent provides for encryption within a virtual machine.
There are a number of features provided the the DataControl agent including:
- Full encrypted path from the VM, through the hypervisor to the storage.
- Support for cloning and replication.
- Dynamic rekey allowing initial encryption or rekey without taking the VM or applications offline.
- Filesystem resize for encrypted devices.
- Encryption of files and support for Amazon S3 storage.
- Migration of encrypted disks between VMs.
- Support for Windows failover clusters.
- Root and swap encryption.
Secure data migration
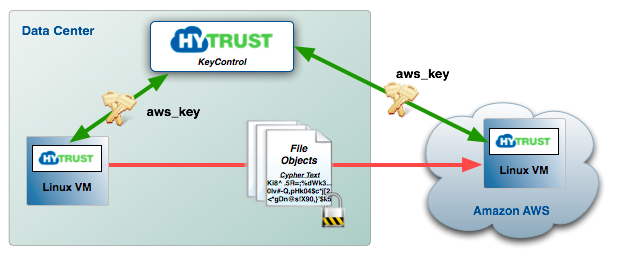
In VMs where the DataControl agent is installed, we support the ability to share keyIDs (encryption keys referenced by a symbolic name) between VMs within the same Cloud VM Set. This allows you to encrypt data and move it between these VMs. Only the VMs within the same Cloud VM Set as the keyIDs are able to decrypt the data. Encryption is on a file-by-file basis, so movement of larger amounts of data can be achieved by zipping/tarring groups of files.
These mechanisms can also be used to encrypt data and move it to cloud storage knowing that only you will be able to decrypt the data on return.
As an extension to the keyID notion, we also provide interfaces for migrating encrypted data between VMs through Amazon S3 storage.
Next chapter - Managing KeyControl Appliances
