Establishing a Trusted Connection with a vSphere-Generated CSR
The following procedure describes how to generate a Certificate Signing Request (CSR) in vSphere and then use that CSR to create a certificate bundle on the HyTrust KMIP server. The KMIP certificate can then be uploaded to vSphere to establish a trusted connection between vSphere and the HyTrust KMIP server.
You can also establish a trusted connection using a KeyControl-generated CSR. For details, see Establishing a Trusted Connection with a KeyControl-Generated CSR.
Note: The following procedure is based on vCenter Web Client in vSphere 6.5. If your version of the vCenter Web Client is different from what is described below, please see your vCenter documentation to determine how to add the KMS cluster.
- In the vSphere Web Client, go to Key Management Servers.
- Select the KMS you want to trust in the list then select All Actions > Establish Trust with KMS.
-
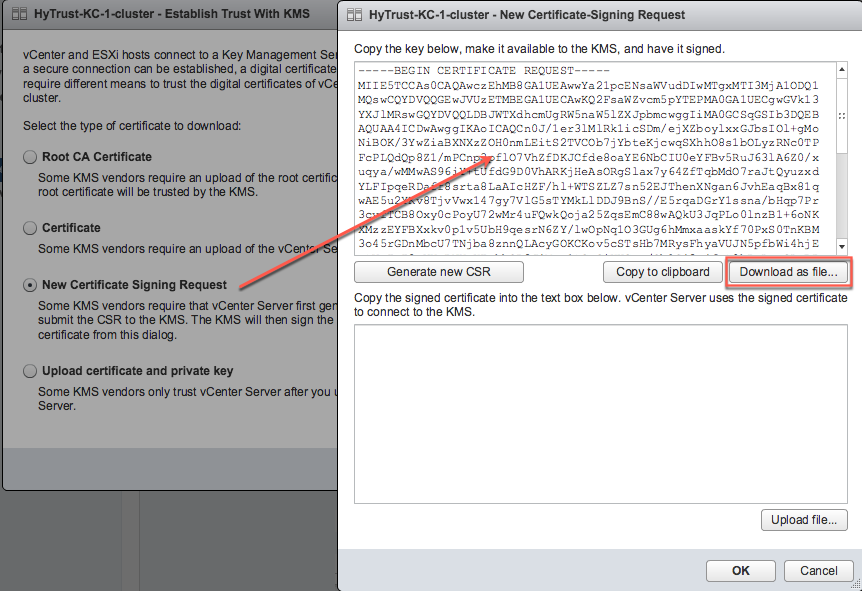
In the Establish Trust with KMS dialog box, select New Certificate Signing Request then click OK.
vSphere creates a CSR and displays it in the New Certificate-Signing Request dialog box.
-
Click Download as file and save the CSR to your computer. By default, vSphere names the CSR file
cluster-name_signed_csr.pem.After you save the file, leave the New Certificate-Signing Request dialog box open.
- Log into the KeyControl webGUI using an account with Security Admin privileges.
- In the top menu bar, click KMIP.
- Click the Client Certificates tab.
- Select Actions > Create Certificate.
-
In the Create a New Client Certificate dialog box:
- Enter a name in the Certificate Name field.
- Set the date on which you want the certificate to expire in the Certificate Expiration field. If the certificate expires, communication between vSphere and KeyControl will be disrupted until a new certificate is uploaded.
- In the Certificate Signing Request (CSR) field, click Load File.
-
Navigate to the vSphere-generated CSR you downloaded earlier in this procedure, select the CSR
pemfile and click Open.Important: Do not enter a password for the certificates. Due to a vSphere limitation, you cannot upload encrypted certificates.
The following example creates a certificate bundle called
KMIPvSphereCertwith a certificate expiration date of December 31, 2019 and that uses the vSphere-generated CSR fileHyTrust-KC-1-cluster_signed_csr.pem.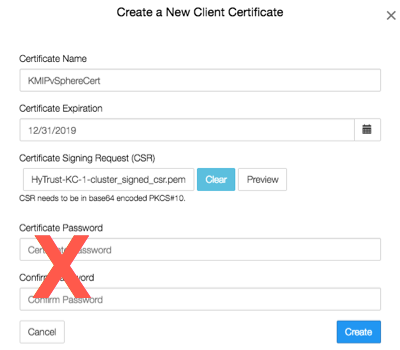
-
Click Create. The webGUI returns to the KMIP Client Certificates tab.
- Select the certificate bundle you just created in the certificate list.
- Select Actions > Download Certificate. The webGUI downloads
<certname_datetimestamp>.zip, which contains a user certification/key file called<certname>.pemand a server certification file calledcacert.pem. - Unzip the file so that you have the
<certname>.pemfile available to upload into vCenter. In the example above the certificate file would be namedKMIPvSphereCert.pem. - Go back to the New Certificate-Signing Request dialog box in the vSphere Web Client and click Upload file.
-
Navigate to the KMIP certificate
<username>.pem, select the file, and click Open. vSphere displays the certificate in the lower half of the New Certificate-Signing Request dialog box.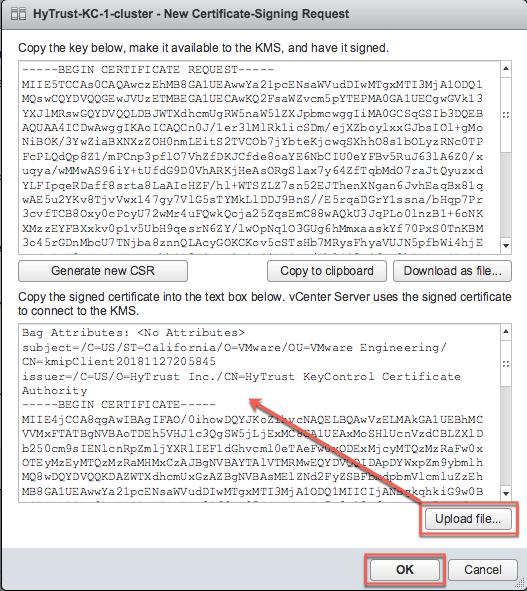
- Click OK and wait until vCenter reports that the connection status for the KMS cluster has changed to "Normal".
- For a multi-node cluster, add the additional KeyControl server IP addresses to the same vSphere KMS cluster to provide a failover mechanism:
- Select the HyTrust KMS you created.
- Click Add KMS.
- In the KMS Cluster field, make sure the HyTrustKMS cluster is selected.
- Enter the server alias, address, and port for the additional KeyControl KMIP server.
- Click OK.
- In the Trust Certificate dialog box, click Trust.
The following illustration shows a HyTrust KMS with three KMIP servers:
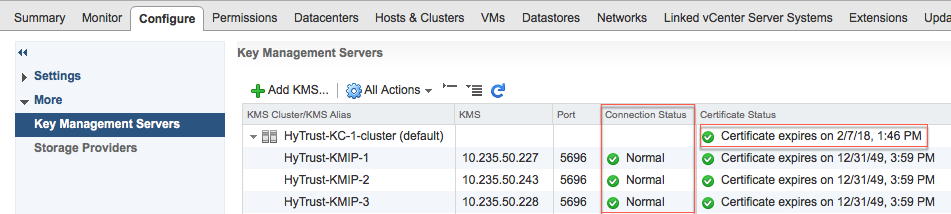
The critical information is the Connection Status for each KMIP server in the cluster and the Certificate Status for the overall KMS cluster. The certificate status for the individual KMIP servers in the cluster can be ignored.
