NFS Client Encryption with FSIDs
If we are running multiple NFS clients and wish to encrypt on each client, we need to ensure that each client is using the same symmetric key. In the following figure, we can see that there are two NFS clients accessing the same directory from the NFS Server. They are both going to share the FSID “NFS_KEY”.
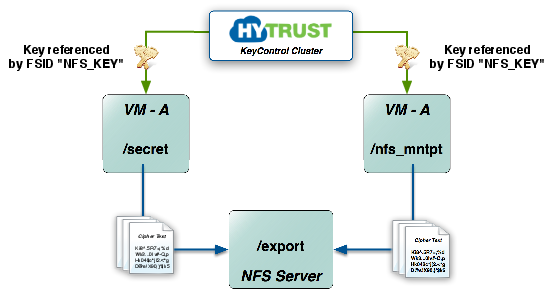
Here are the steps that must be followed in order to for both VMs to access the same NFS mountpoint:
- Mount the NFS-exported directory on each VM
- Create an FSID on one of the client VMs
- Enable sharing of the FSID in the GUI (allows other VMs to access it)
- Run
hcl addfson both of the VMs
So from VM-A shown in the figure above, run the following:
# hcl fsid -c "NFS_KEY" -d "This is a shared key" # fsid -l FSID Algorithm Description ----- --------- ----------- NFS_KEY AES-256 This is a shared key my_local_key AES-256 this is a key just for this VM my_nfs_key AES-256 NFS key # hcl addfs NFS_KEY /secret
Note that the exported filesystem must have already been mounted on /secret. Now if we run the following on VM-B:
# hcl fsid -l FSID Algorithm Description ----
you can see that no FSIDs are listed even though this VM is in the same Cloud VM Set.
At this point, we go to the GUI, select the appropriate Cloud VM Set, select the FSIDs tab and select the appropriate FSID, in this case “NFS_KEY”.
Change “Shared” to “Yes” and click Save. Now if you go back to VM-B, we will be able to see the FSID:
# hcl fsid -l FSID Algorithm Description ---- --------- ----------- NFS_KEY AES-256 This is a shared key
You can therefore access the contents as follows:
# hcl addfs NFS_KEY /nfs_mtpt
Now let’s create some files and access them:
VM-A# echo hello > /secret/a-file VM-B# cat /nfs_mtpt/a-file hello VM-B# echo "how are you?" > /nfs_mtpt/b-file VM-A# cat /secret/b-file how are you?
If we look on the NFS server, we only see encrypted filenames:
# ls /nfs ECRYPTFS_FNEK_ENCRYPTED.FWZJQXtCp3pjBkaFaEsRCsBcjOxB13Rf0xJu66WoxAVbkwXf5f5x.WUYJk-- ECRYPTFS_FNEK_ENCRYPTED.FWZJQXtCp3pjBkaFaEsRCsBcjOxB13Rf0xJukdu2eF4grFOJ-oZGmxcqak--
If we look at the contents of a file, we will see that it is encrypted.
Note that we do nothing to provide synchronization between files accessed by multiple NFS clients.

