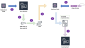
Azure BYOK Process
This section describes the workflow that occurs in the KeyControl Vault for Cloud Keys when you use BYOK for Azure.
Azure keys can be hardware-protected or software-protected.
Hardware-Protected Key
-
A Cloud Key is created with key material in the KeyControl Vault for Cloud Keys.
If HSM is configured, the key is generated and wrapped with a root key on the HSM.
-
A Key Encryption Key (KEK) is created in Azure KeyVault in your chosen key vault.
-
The RSA-2048 wrapping public key and the KEK ID from the Azure KeyVault are downloaded.
-
The RSA-2048 wrapping public key and the KEK ID are imported into the KeyControl Vault for Cloud Keys.
-
The imported wrapping key is used to wrap the asymmetric key and create a blob.
-
The asymmetric key is imported into Azure KeyVault using the KEK ID from Step 3.
Software-Protected Key
-
A Cloud Key with key material is created in the KeyControl Vault for Cloud Keys.
If HSM is configured, the key is generated and wrapped with a root key on the HSM, and protected by the HSM in the KeyControl Vault for Cloud Keys.
-
The asymmetric key is imported in Azure KeyVault.
The communication between KeyControl Vault for Cloud Keys and Azure is protected by SSL/TSL.