Entrust KeyControl Vault
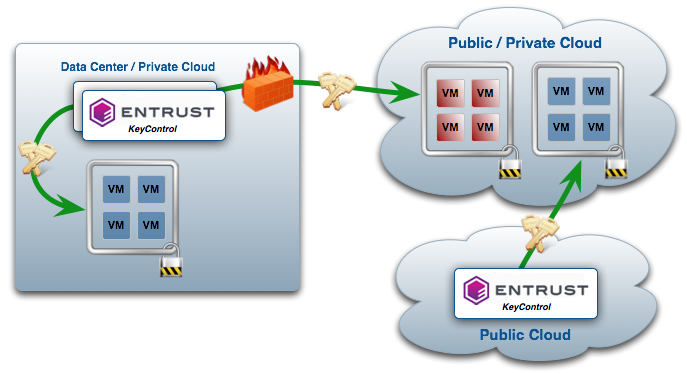
At the heart of every Entrust KeyControl Vault deployment is an active-active cluster of KeyControl Vault nodes that manage encryption keys for virtual Linux and Windows machines.
KeyControl Vault features include:
- An active-active cluster for high availability. Any changes made to any KeyControl Vault node in the cluster are automatically reflected on all nodes in the cluster.
-
Clustered object store protecting keys, policies and configuration data. All objects are encrypted and ultimately wrapped with an Admin Key.
The Admin Key uses a software-based "n of m" backup. This prevents KeyControl Vault backups from being stolen and installed on new hardware.
- Nodes can join or leave the cluster without affecting KeyControl Vault's ability to deliver encryption keys.
- A KeyControl Vault cluster moves into degraded mode (read only) on network disconnect or failure. While in degraded mode, any KeyControl Vault node can still serve requests for existing keys and policies from VMs where the Policy Agent is installed. However, new encryption keys cannot be created.
- Each Policy Agent communicates with any KeyControl Vault node, switching between them if they detect a non-responsive KeyControl Vault node.
- All system components of the KeyControl Vault are encrypted.
- Support for admin authentication via local accounts with strict password controls or via accounts stored in LDAP (including Microsoft AD).
- Support for Alerts in environments with and without email access.
- Full-featured command line utilities (
hicliandhcl). - A rich RESTful API.
