Tokenization Vault Overview
Note: Beginning with release 10.2, the Encryption policy no longer exists. You can encrypt blocks of unstructured data using keys.
The Tokenization vault lets you configure the following policy types:
-
Tokenization—Format-preserving encryption. For example:
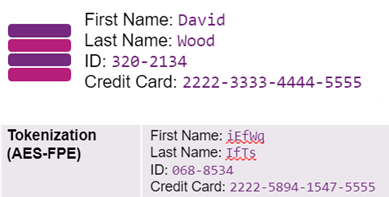
Tokenization can be reversed to retrieve the sensitive data from the token.
-
Masking—Masks data. You can set the masking character, plus a prefix and suffix value if you want to preserve some of the data. For example:
Original credit card number:
2222-3333-4444-5555Masked credit card number:
22##-####-####-##55Masking is one-way encryption. You cannot retrieve the data from the token.
An example use case is exporting data and generating reports with the sensitive data masked.
Note: The KeyControl Tokenization Vault webGUI has an automatic timeout value of 15 minutes.
