Cryptographic Security Platform Vault for Cryptographic APIs Overview
Note: Beginning with release 10.2, the Encryption policy no longer exists. You can encrypt blocks of unstructured data using keys.
The Cryptographic Security Platform Vault for Cryptographic APIs lets you configure the following policy types:
-
Tokenization—Format-preserving encryption. For example:
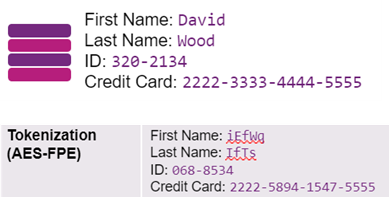
Tokenization can be reversed to retrieve the sensitive data from the token.
Each Cryptographic Security Platform Vault for Cryptographic APIs cluster (including all vaults in the cluster) has been tested to support 10,000 tokenization key objects, and can tokenize 1 million records at once.
-
Masking—Masks data. You can set the masking character, plus a prefix and suffix value if you want to preserve some of the data. For example:
Original credit card number:
2222-3333-4444-5555Masked credit card number:
22##-####-####-##55Masking is one-way encryption. You cannot retrieve the data from the token.
An example use case is exporting data and generating reports with the sensitive data masked.
Important: If you plan to manage Entrust Elliptic Curve Cryptography (ECC) keys in a Cryptographic Security Platform Vault for Cryptographic APIs that is protected by an nShield XC HSM, you must have an ECC license for that HSM.
The Cryptographic Security Platform Vault for Cryptographic APIs webGUI has an automatic timeout value of 15 minutes.
