Supported Authentication Modes
HyTrust CloudControl (CloudControl) authenticates users for every attempted login and/or operation on vCenter Server. It provides three authentication modes, in which it employs different authentication methods in combination with different vCenter settings. Those authentication modes are:
-
CloudControl Service Account (default) and best practice
-
Pass through without CloudControl Service Account
-
Pass through with CloudControl Service Account
The following table provides detailed information about required user account configurations on vCenter Server, credentials used for vCenter operations, restrictions on object views, and recommended use for each of the modes.
|
Authentication Mode |
Required Account Settings |
Credentials used for vCenter Operations |
Restrictions on Object Views |
Recommended Use |
|
Use CloudControl Service Account |
Only the Service Account must be provisioned on vCenter Server for CloudControl purposes. |
Service Account |
No restrictions on object views |
Recommended, default setting |
|
Use pass through without CloudControl Service Account |
Every user must be configured and provisioned with appropriate privileges on vCenter Server. |
Active Directory Credentials of the authenticated user |
Object views restricted based on user privileges on vCenter Server |
For restricted object views |
|
Use pass through with CloudControl Service Account |
Provision individual users with login privileges only on vCenter Server. Provision Service Account normally. |
Service Account |
No restrictions on object views |
Smart Card authentication |
CloudControl Service Account
CloudControl uses Service Account credentials to integrate directly with Active Directory (AD) via LDAP protocols. It also uses the Service Account to query Active Directory and confirm the appropriate group membership for the users. For more information on how to configure the Service Account in Active Directory, see Service Account Privileges.
IWA Support
Integrated Windows Authentication (IWA) is commonly used in the context of alternative credential options such as Smart Card and PIV-II card authentication. Unlike basic authentication, IWA does not prompt for a user name and password. Instead, it uses the current Windows login information on the client to authenticate users.
Smart Card Support
For Smart Card users, a Windows session is initiated using their Smart Card credentials. Smart Card users log in to the vSphere client with the Use Windows session credentials option selected. IWA passes the same Smart Card credentials that were used to initiate the Windows session, to the vSphere client. The vSphere client passes the authentication token sent by IWA to CloudControl, which then passes it to vCenter Server.
Authentication Modes
Use CloudControl Service Account (default)
The following figure describes the authentication process using CloudControl Service Account.
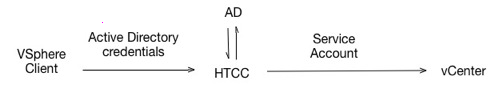
In this authentication mode, users login to the vSphere client using their Active Directory credentials. CloudControl authenticates users’ AD credentials and logs in to vCenter Server using the Service Account credentials provided in the CloudControl configuration. The Service Account must be configured on vCenter Server and CloudControl performs all operations using the Service Account credentials.
Users are not required to exist or be configured on vCenter Server. The user's view of objects is not restricted.
Smart Card Authentication
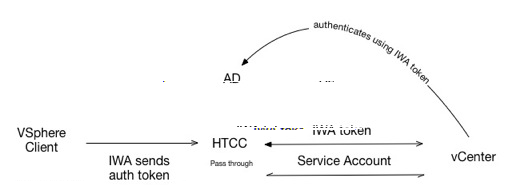
Smart Card users login to the vSphere client with the IWA option enabled. This causes the vSphere client and CloudControl to pass their Windows session authentication token directly to vCenter Server. vCenter Server authenticates the user against Active Directory. After authentication, all operations on the vCenter Server are authorized based on the CloudControl policy and CloudControl performs them using the Service Account credentials.
Use pass through without CloudControl Service Account
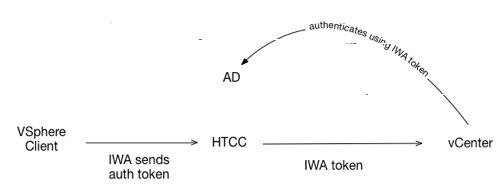
The following figure describes pass through without using CloudControl Service Account.
Use pass through without CloudControl Service Account
In this authentication mode, users login to the vSphere client using their AD credentials. CloudControl authenticates them against Active Directory, and logs in to vCenter Server using their AD credentials. CloudControl performs operations on vCenter Server with the users’ AD credentials.
In this authentication mode, every user must exist and be configured with appropriate permissions on vCenter Server. The user's view of objects is determined by their role defined on vCenter Server.
Smart Card Authentication
Smart Card users login to the vSphere client with the IWA option enabled. This causes the vSphere client and CloudControl to pass their Windows session authentication token directly to vCenter Server. vCenter Server authenticates the user against Active Directory. After authentication, all operations on vCenter Server are authorized based on the CloudControl policy and CloudControl performs them with the user’s Active Directory credentials.
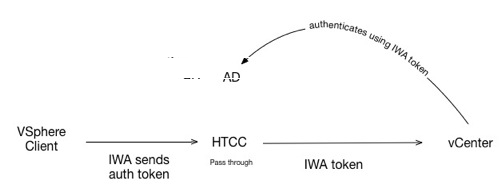
Use pass through with CloudControl Service Account
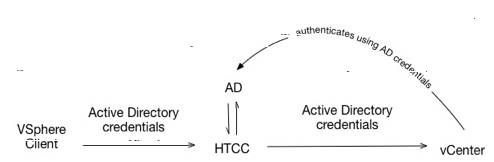
The following figure describes pass through using CloudControl Service Account.
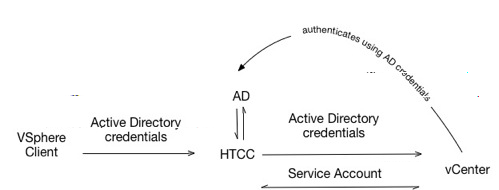
In this authentication mode, users login to the vSphere client using their Active Directory credentials. CloudControl authenticates them against Active Directory and also passes the credentials to vCenter Server for authentication. Once authenticated, CloudControl performs operations using the Service Account credentials.
In this mode, every user must exist and be configured with login permissions on vCenter Server. The user's view of objects is not restricted.
Smart Card Authentication
Smart Card users login to the vSphere client with the IWA option enabled. This causes the vSphere client and CloudControl to pass their Windows session authentication token directly to vCenter Server, which authenticates the user against Active Directory. After authentication, all operations on vCenter Server are authorized according to the CloudControl policy and CloudControl performs them using the Service Account credentials.